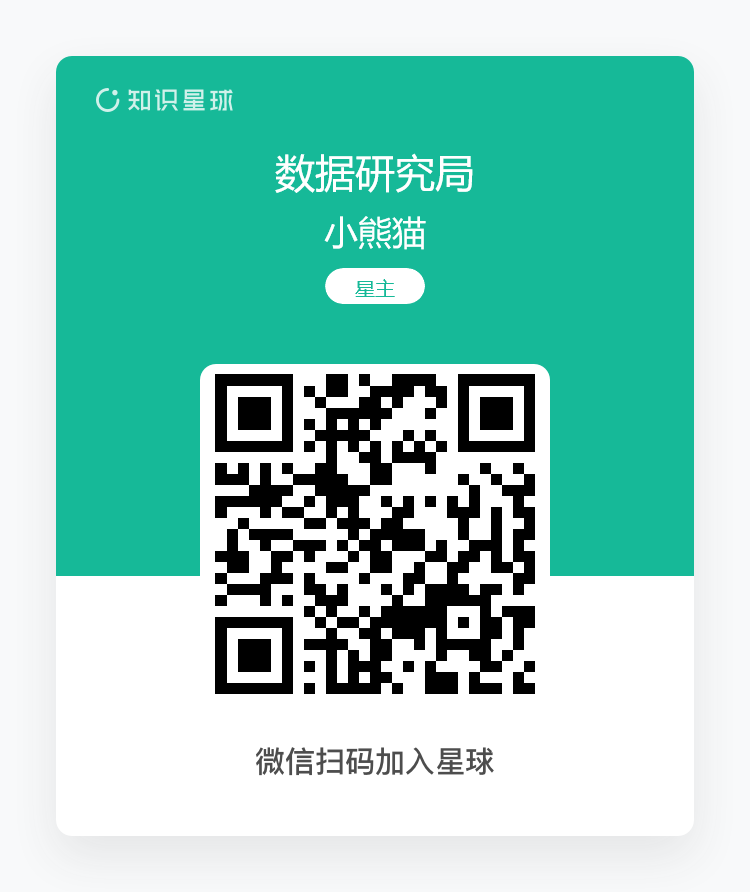
DETERRENCE BY DETECTION: A KEY ROLE FOR UNMANNED AIRCRAFT SYSTEMS IN GREAT POWER COMPETITION THOMAS G. MAHNKEN TRAVIS SHARP GRACE B. KIM DETERRENCE BY DETECTION: A KEY ROLE FOR UNMANNED AIRCRAFT SYSTEMS IN GREAT POWER COMPETITION THOMAS G. MAHNKEN TRAVIS SHARP GRACE B. KIM 2020 ABOUT THE CENTER FOR STRATEGIC AND BUDGETARY ASSESSMENTS (CSBA) The Center for Strategic and Budgetary Assessments is an independent, nonpartisan policy research institute established to promote innovative thinking and debate about national security strategy and investment options. CSBA’s analysis focuses on key questions related to existing and emerging threats to U.S. national security, and its goal is to enable policymakers to make informed decisions on matters of strategy, security policy, and resource allocation. ©2020 Center for Strategic and Budgetary Assessments. All rights reserved. ABOUT THE AUTHORS Thomas G. Mahnken is President and Chief Executive Officer of the Center for Strategic and Budgetary Assessments. He is a Senior Research Professor at the Philip Merrill Center for Strategic Studies at The Johns Hopkins University’s Paul H. Nitze School of Advanced International Studies (SAIS) and has served for over 20 years as an officer in the U.S. Navy Reserve, to include tours in Iraq and Kosovo. He currently serves as a member of the Congressionally-mandated National Defense Strategy Commission and as a member of the Board of Visitors of Marine Corps University. His previous government career includes service as Deputy Assistant Secretary of Defense for Policy Planning from 2006–2009, where he helped craft the 2006 Quadrennial Defense Review and 2008 National Defense Strategy. He served on the staff of the 2014 National Defense Panel, 2010 Quadrennial Defense Review Independent Panel, and the Commission on the Intelligence Capabilities of the United States Regarding Weapons of Mass Destruction. He served in the Defense Department’s Office of Net Assessment and as a member of the Gulf War Air Power Survey. In 2009 he was awarded the Secretary of Defense Medal for Outstanding Public Service and in 2016 the Department of the Navy Superior Civilian Service Medal. Travis Sharp is a Research Fellow at the Center for Strategic and Budgetary Assessments. He directs the budget program and works to educate and inform policymakers, senior leaders, and the general public about the defense budget and issues pertaining to resourcing national security. He also serves as an officer in the U.S. Navy Reserve while completing his Ph.D. in security studies at Princeton University’s Woodrow Wilson School of Public and International Affairs. Travis has held positions with academic and policy organizations, including George Washington University’s Institute for Security and Conflict Studies, West Point’s Modern War Institute, the Office of the Secretary of Defense, the Center for a New American Security, and the Center for Arms Control and Non-Proliferation. He has published think tank monographs, journal articles, and commentaries on defense spending and strategy, cybersecurity, and military-to-military contacts between great power rivals, the topic of his dissertation. Mr. Sharp is a past recipient of the Sasakawa Young Leaders Fellowship, the A.B. Krongard and John Parker Compton Fellowships at Princeton, the 1LT Bacevich Fellowship at CNAS, the Harold Rosenthal Fellowship in International Relations, and the Herbert Scoville Peace Fellowship. Grace B. Kim is a Senior Analyst at the Center for Strategic and Budgetary Assessments (CSBA), where she focuses on U.S. and allied defense strategies and operational concepts, long-term strategic competition, and trends in future warfare in East Asia and Europe and leads CSBA’s Korea-focused analysis. Ms. Kim has previous work experience supporting U.S. government counter-proliferation and sanctions policies in East Asia and the Middle East in the Office of the Secretary of Defense for Policy (OSDP) Countering Weapons of Mass Destruction office and Treasury Department’s International Affairs East Asia office. She has also worked at the Institute for the Study of War as a Turkish Linguist on the Syria Team and spent four years living and working in Turkey analyzing U.S. and NATO security policy in Europe and the Middle East as a Fulbright fellow and researcher at the Istanbul-based Centre for Economics and Foreign Policy Studies. Ms. Kim also has held fellowships with the George Washington University Institute for Korean Studies and Pacific Forum, where she is currently a Nonresident James A. Kelly Korea Fellow and Young Leader. ACKNOWLEDGMENTS The authors would like to thank the CSBA leadership and staff for their assistance with this report. Special thanks go to Billy Fabian, whose ideas and insights laid the foundation for developing the “deterrence by detection” operational concept and without whom the analysis detailed in this report would not have been possible. The authors would also like to thank CDR Kevin Chlan, Evan Montgomery, David Zikusoka, and a series of anonymous reviewers for their comments and suggestions. The analysis and findings presented here are solely the responsibility of the authors. CSBA receives funding from a broad and diverse group of contributors, including private foundations, government agencies, and corporations. A complete list of these organizations can be found on our website at www.csbaonline.org/about/contributors. Cover: Composite design by Grace B. Kim with photographs courtesy of General Atomics. Contents EXECUTIVE SUMMARY . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . i Background. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . i Implementing the “Deterrence by Detection” Operational Concept. . . . . . . . . . . . . . . . . . . . . ii CHAPTER 1: THE INFORMATION DIMENSION OF DETERRENCE. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1 Problem Statement. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1 Chapter Roadmap. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 Denying Opportunistic Aggression: A Key Operational Challenge . . . . . . . . . . . . . . . . . . . . . . 3 The Concept of “Deterrence by Detection”. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 UAS Capabilities. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9 Advantages and Disadvantages of UAS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16 Conclusion. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18 CHAPTER 2: IMPLEMENTING THE “DETERRENCE BY DETECTION” CONCEPT . . . . . . . . . . . . . . . . . . . . . . 19 Attributes of an Enhanced ISR Network. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19 Priority Geographic Areas for ISR Missions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22 Implementing “Deterrence by Detection” . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29 Estimate of Required UAS Inventory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32 Role of Allies and Partners. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33 Estimate of Budgetary Costs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40 Conclusion. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41 LIST OF ACRONYMS. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42 FIGURES FIGURE 1: ISR ARCHITECTURE USING UNMANNED AIRCRAFT SYSTEMS . . . . . . . . . . . . . . . . . . . . . . 20 FIGURE 2: SUGGESTED UAS ORBITS IN THE WESTERN PACIFIC. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30 FIGURE 3: SUGGESTED UAS ORBITS IN EASTERN EUROPE . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31 TABLES TABLE 1: UAS GROUP CLASSIFICATIONS AND CHARACTERISTICS. . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 TABLE 2: REQUIRED UAS INVENTORY FOR DETERRENCE BY DETECTION CONCEPT, BY GEOGRAPHIC AREA. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32 TABLE 3: REQUIRED UAS INVENTORY FOR DETERRENCE BY DETECTION CONCEPT BY AIRCRAFT TYPE. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40 www.csbaonline.org i Executive Summary In an era of renewed great power competition, one of the most significant challenges the United States and its allies face is the need to deny China or Russia the ability to launch opportunistic acts of aggression against an ally or partner in the Western Pacific or Eastern Europe. This report proposes a “deterrence by detection” operational concept to deter Chinese and Russian aggression, one that uses a network of existing non-stealthy longendurance unmanned aircraft systems (UAS) to maintain real-time, persistent situational awareness in key geographic areas in the Western Pacific and Eastern Europe. Background China and Russia are developing the ability to launch aggression rapidly against states on their periphery under the cover of increasingly capable reconnaissance-strike networks. The geographic friction points in the Western Pacific and Eastern Europe that are most likely to devolve into crisis and conflict lie much closer to Russia and China than they do to the continental United States. With only limited warning, Beijing or Moscow could exploit their time-distance advantage to seize allied territory before the United States and its allies could respond, thereby creating a fait accompli that would be difficult to reverse after the fact. The U.S. armed forces are poorly configured to meet these challenges, which require longduration monitoring rather than episodic coverage. Although the Defense Department has the requisite existing and near-term capabilities to do so, namely non-stealthy long-endurance UAS, it needs to develop new concepts of operations and organizations to employ those capabilities effectively. The new concept for employing UAS to deter opportunistic aggression, which we call “deterrence by detection,” will also benefit greatly from approaches that allow allies and partners to participate fully. Implementing the concept of “deterrence by detection” will require an intelligence, surveillance, and reconnaissance (ISR) network composed of systems that are cost-effective, persistent, and interoperable with a broad array of allies and partners. Real-time situational awareness is critical to countering the twin challenges of sub-conventional gray zone aggression and a conventional fait accompli gambit promptly and effectively. UAS conducting ISR ii CSBA | DETERRENCE BY DETECTION missions could provide increased warning of a pending Chinese or Russian attack, thereby helping to ensure that forward postured forces are prepared to respond decisively. By increasing warning time, UAS would help mitigate the United States’ time-distance disadvantage, thereby allowing the United States and its allies to mass sufficient combat power to prevent a fait accompli.” Implementing the “Deterrence by Detection” Operational Concept This study identifies three priority geographic areas in the Asia-Pacific and three in Europe that are best suited for long-endurance unmanned aerial reconnaissance: the Taiwan Strait, South China Sea, and East China Sea in the Asia-Pacific and the Baltics, Black Sea, and eastern Mediterranean Sea in Europe. In addition to the Taiwan Strait, South China Sea, and East China Sea, the ability to observe military activity persistently along the Chinese coastline would enhance situational awareness and could alert the United States and its Asian allies and partners to an impending Chinese attack. Surveilling China’s activities would also serve the purpose of monitoring, and thus potentially deterring, other opportunistic actors in the region, such as North Korea and Russia. The UAS for the “deterrence by detection” concept would come from U.S., allied, and partner country inventories and would operate in national groups and potentially as part of a coalition network. Additional UAS would be required for ISR missions beyond those described here. The total number of UAS airframes needed to implement a “deterrence by detection” strategy in the Asia-Pacific and European theaters is well within reach. Indeed, a virtue of the concept is that it employs capabilities that the United States already possesses but that have been underutilized in the context of great-power competition because their value in that context has not been appreciated. CSBA analysis shows that implementing “deterrence by detection” would require 46 airframes in the Western Pacific and another 46 in Europe, for a total of 92 aircraft. Additional UAS would be required for ISR missions beyond those described here.1 The United States and its allies and partners could meet the inventory requirement by shifting existing aircraft from other theaters and missions to the Western Pacific and Europe and by assigning some of the aircraft the United States is already procuring to new missions. The decisions will depend on each aircraft’s production status and the size of the existing fleet. We estimate that the annual operating cost for the 92 UASs would total approximately $1.4 billion per year, based on Congressional Budget Office figures. Since the aircraft would come from the existing inventory, not from new purchases, the operating cost represents 1 For recent CSBA assessments of overall UAS inventory requirements, see Gunzinger, et. al., An Air Force for An Era of Great Power Competition; Mark Gunzinger, Carl Rehberg, and Lukas Autenried, Five Priorities for the Air Force’s Future Combat Air Force (Washington, D.C.: Center for Strategic and Budgetary Assessments, 2020). www.csbaonline.org iii money DoD would have spent anyway to keep the aircraft flying (assuming it kept them flying). For this reason, implementing “deterrence by detection” should not require any spending increases.2 Rather, implementing the concept should only require DoD to change what it does with the aircraft it already pays for. Split among the United States and its many allies and partners in the Western Pacific and Europe, the estimated cost per country should remain affordable relative to the expected security gains. In sum, the United States and its allies face operational challenges in competing against China and Russia, including the ability to deter opportunistic acts of aggression by subconventional forces that would result in a fait accompli. “Deterrence by detection,” based upon the idea that our adversaries are less likely to commit opportunistic acts of aggression if they know they are being watched constantly and that their actions can be publicized widely, can generate and maintain real-time situational awareness that can contribute to meeting the fait accompli challenge. Non-stealthy unmanned ISR aircraft capable of conducting wide-area persistent surveillance missions are best suited to implementing “deterrence by detection” by the United States, its allies, and partners. Although this concept is far from a panacea, it is a realistic, effective, and affordable step in the right direction. 2 This estimate multiplies the UAS inventories in Table 3 by the direct and indirect cost figures included in Congressional Budget Office, The U.S. Military’s Force Structure: A Primer (July 2016), p. 100. Due to data limitations, the estimate assumes the MQ-4C has the same operating cost as the RQ-4. The estimate converts CBO’s per squadron cost to per aircraft cost and adjusts the figures to FY 2019 dollars based on DoD, National Defense Budget Estimates for FY 2019 (April 2018), Table 5-6, pp. 62-63. The calculation proceeds as follows: (34 MQ-9s x $7.8m) + (26 MQ-4Cs x $25.1m) + (18 RQ-4s x $25.1m) + (14 MQ-1Cs x $4.3m) = ~$1.4b. iv CSBA | DETERRENCE BY DETECTION www.csbaonline.org 1 CHAPTER 1 The Information Dimension of Deterrence One of the most significant challenges the United States and its allies face is the need to deny China or Russia the ability to launch opportunistic acts of aggression resulting in a successful fait accompli against an ally or partner in the Western Pacific or Eastern Europe. This chapter proposes a “deterrence by detection” operational concept to deter Chinese and Russian aggression by using a network of existing non-stealthy long-endurance unmanned aircraft systems (UAS) to maintain real-time, persistent situational awareness in key geographic areas in the Western Pacific and Eastern Europe. Problem Statement Today and for the foreseeable future, the most important and consequential challenge facing the United States and its allies will be the need to compete with, deter, and potentially fight China and Russia. This strategic imperative translates into a series of operational challenges that are the result of a combination of the tyranny of distance and eroding military balances.3 Although the Pacific and Atlantic oceans protect the United States against attack, the immense distance between North America and the European and Asian continents guarantees that the objects of Chinese or Russian aggression lie closer to them than to the United States. Delivering military force across the Pacific and Atlantic oceans has never been easy, even for a country as powerful as the United States. The problem has worsened as America’s chief rivals, China and Russia, have bolstered their ability to harm American interests rapidly with little warning. Whereas the United States has historically used alliances and forward-based forces to undermine the tyranny of distance, regional military balances are increasingly unfavorable to the United States and its allies. China and Russia 3 Thomas G. Mahnken, Grace B. Kim, and Adam Lemon, Piercing the Fog of Peace: Developing Innovative Operational Concepts for a New Era (Washington, D.C.: Center for Strategic and Budgetary Assessments, 2019), p. 14. 2 CSBA | DETERRENCE BY DETECTION have spent years observing the American way of war and have developed operational concepts and capabilities tailored to preventing the United States from projecting power unmolested. Moreover, the Chinese and Russian nuclear arsenals may serve both to deter U.S. intervention as well as to limit its scope and intensity should it nonetheless occur. As a result, Chinese or Russian leaders may believe that they can achieve a quick, decisive victory against regional adversaries before the United States can intervene. Under these circumstances, American political leaders might face the unenviable choice of doing nothing or escalating to higher levels of violence. Either way, the national interests of both the United States and its closest allies would suffer dramatically. One of the most significant challenges the United States and its allies thus face is the need to deny China or Russia the ability to launch opportunistic acts of aggression. However, U.S. forces are poorly configured to prevent China and Russia from achieving a fait accompli against an ally or partner in the Western Pacific or Eastern Europe.4 History shows that deterrence is more likely to fail when an aggressor believes it can pull off a fait accompli successfully. If the U.S. military fails to prepare now for a potential fait accompli attempt, it will cede the ability to deter and, if necessary, defeat acts of aggression. Developing innovative operational concepts and fielding new organizations and capabilities to overcome these challenges should become the urgent focus of Defense Department investment. As the National Defense Commission noted in its report to Congress: The United States needs more than just new capabilities; it urgently requires new operational concepts that expand U.S. options and constrain those of China, Russia, and other actors. Operational concepts constitute an essential link between strategic objectives and the capability and budgetary priorities needed to advance them. During the Cold War, the United States developed detailed operational concepts to overcome daunting challenges in Europe and elsewhere. Innovative concepts are once again needed because Russia and China are challenging the United States, its allies, and its partners on a far greater scale than has any adversary since the Cold War’s end. The unconventional approaches on which others rely, such as hybrid warfare (warfare combining conventional and unconventional elements), grayzone aggression (coercion in the space between peace and war), and rapid nuclear escalation demand equally creative responses. In other words, maintaining or reestablishing America’s competitive edge is not simply a matter of generating more resources and capabilities; it is a matter of using those resources and capabilities creatively and focusing them on the right things (emphasis added). Unfortunately, the innovative operational concepts we need do not currently appear to exist. The United States must begin responding more effectively to the 4 This report uses fait accompli in the sense of “a quick, decisive transformation of the situation” before the other side can immediately react. For definitional discussion see Ahmer Tarar, “A Strategic Logic of the Military Fait Accompli,” International Studies Quarterly 60, no. 4, December 2016, pp. 743–744. www.csbaonline.org 3 operational challenges posed by our competitors and force those competitors to respond to challenges of our making.5 In an era of constrained resources, those concepts and capabilities that offer the greatest ability to meet these challenges should receive preferential funding over those that do not.6 It would be particularly beneficial for the United States to identify, develop, and implement concepts that make effective use of the forces and capabilities it already possesses, and particularly those that are not heavily utilized in other concepts for great power competition. Chapter Roadmap This chapter performs three interrelated tasks. First, it outlines the operational challenge facing the United States and its allies. The discussion remains succinct, endeavoring only to set up the operational concept analysis in the next chapter. Readers interested in additional detail should consult other recent CSBA monographs that describe innovative operational concepts.7 Second, it describes how the concept of “deterrence by detection” based upon generating and maintaining real-time situational awareness can contribute to solving the fait accompli challenge. Finally, the chapter summarizes the capabilities of four existing UAS and then assesses the advantages and disadvantages of using those capabilities to perform ISR missions in great power competition. A recent CSBA report, Tightening the Chain, outlined a strategy of Maritime Pressure and described an “Inside-Out” operational concept and force posture to allow the United States and its allies to deter opportunistic aggression in the Western Pacific.8 This report complements that study in that it focuses on the information dimension of deterrence. Moreover, the capabilities and concepts described in this report complement those in Tightening the Chain. In particular, the UAS network described in this report forms a key element of the peacetime Inside Force described in Tightening the Chain. Denying Opportunistic Aggression: A Key Operational Challenge The end of the Cold War ushered in a period of U.S. military dominance, demonstrated vividly by the 1991 Gulf War, the Balkan wars, the overthrow of the Taliban in Afghanistan 5 National Defense Strategy NDS Commission, Providing for the Common Defense: The Assessment and Recommendations of the National Defense Strategy Commission (Washington, DC: United States Institute of Peace, 2018), p. vii. 6 Piercing the Fog of Peace, p. 50. 7 Recent research along these lines includes Mark Gunzinger and Carl Rehberg, Air and Missile Defense at a Crossroads: New Concepts and Technologies to Defend America’s Overseas Bases (Washington, DC: Center for Strategic and Budgetary Assessments, 2018). 8 Thomas G. Mahnken, Travis Sharp, Billy Fabian, and Peter Kouretsos, Tightening the Chain: Implementing a Strategy of Maritime Pressure in the Western Pacific (Washington, DC: Center for Strategic and Budgetary Assessments, 2019). 4 CSBA | DETERRENCE BY DETECTION following the September 11, 2001 terrorist attacks, and the overthrow of Saddam Hussein in Iraq in 2003. U.S. competitors such as China and Russia have studied American operations intently and have developed concepts and capabilities to help them avoid the fate of previous U.S. adversaries.9 Two particularly worrisome developments involve attempts to achieve their objectives without drawing a conventional response and the development of the means to carry out a rapid attack upon neighboring states, presenting the United States and its allies with a fait accompli. China and Russia have employed sub-conventional gray zone aggression to erode international norms, undermine the U.S-led rules-based order, and shift the balance of power in their favor, all without sparking open armed conflict with the United States or its allies.10 China has used paramilitary naval forces, such as fishing fleets and its maritime militia, to harass its maritime neighbors’ military and commercial vessels in order to further its claims over disputed territory. It has flown fighter jets across the median line of the Taiwan Strait. It has conducted sorties with its bombers over the Miyako Strait near Japan.11 It has also created and militarized artificially built islands in the disputed waters of the South China Sea.12 Russia, for its part, has employed military and paramilitary forces to seize the Crimean Peninsula and support a separatist insurgency in eastern Ukraine. It has used jammers and other forms of electronic attack to disrupt NATO exercises. It has also conducted influence operations to interfere in the internal politics of alliance members, including the United States.13 Such operations often prove difficult to identify as they unfold, particularly since China and Russia obscure their motives and roles. Consequently, the United States and its allies have struggled to counter their actions before it is already too late. China and Russia are also developing the ability to launch aggression rapidly against states on their periphery under the cover of increasingly capable reconnaissance-strike networks. Both Beijing and Moscow have developed capabilities to thwart U.S. efforts to project 9 Ian Easton, “China’s Top 5 War Plans,” National Interest, January 12, 2019, available at https://nationalinterest. org/ blog/buzz/chinas-top-5-war-plans-41332; Michael Kofman, “It’s Time to Talk About A2/AD: Rethinking the Russian Military Challenge,” War on the Rocks, September 5, 2019, available at https://warontherocks.com/2019/09/ its-time-to-talk-about-a2-ad-rethinking-the-russian-military-challenge. 10 Ross Babbage, Stealing a March: Chinese Hybrid Warfare in the Indo-Pacific: Issues and Options for Allied Defense Planners, Volume I (Washington, DC: Center for Strategic and Budgetary Assessments, 2019); and Ross Babbage, Winning Without Fighting: Chinese and Russian Political Warfare Campaigns and How the West Can Prevail (Washington, DC: Center for Strategic and Budgetary Assessments, 2019). 11 Ben Westcott, “Taiwan scrambles jets to confront Chinese fighters after rare incursion,” CNN, April 1, 2019, https:// www.cnn.com/2019/04/01/asia/china-japan-taiwan-jets-intl/index.html. 12 Council on Foreign Relations, “Territorial Disputes in the South China Sea,” Global Conflict Tracker, last updated August 10, 2019, https://www.cfr.org/interactive/global-conflict-tracker/conflict/territorial-disputes-south-china-sea. 13 Gerard O’Dwyer, “Norway accuses Russia of jamming its military systems,” Defense News, March 8, 2019, https://www. defensenews.com/global/europe/2019/03/08/norway-alleges-signals-jamming-of-its-military-systems-by-russia/. www.csbaonline.org 5 military power.14 The geographic friction points in the Western Pacific and Eastern Europe that are most likely to devolve into crisis and conflict lie much closer to Russia and China than they do to the continental United States. With only limited warning, China or Russia could exploit their time-distance advantage to seize allied territory before the United States and its allies could respond, thereby creating a fait accompli that would be difficult to reverse after the fact. The U.S. armed forces are poorly configured to meet these challenges, which require long-duration monitoring rather than episodic coverage. They possess multiple information-gathering platforms capable of persistent wide-area airborne surveillance but too few of them are dedicated to monitoring sub-conventional acts of aggression by great power competitors. As a result, they can deploy only periodically. Moreover, these multi-function systems are expensive, which reinforces the tendency to under-invest in them. The expense of these platforms also fosters risk aversion because they would be costly to lose. The Services’ reliance on expensive, and hence scarce, platforms is at odds with the need for long-duration monitoring of numerous key areas. Here as in other areas, the United States and its allies find themselves on the wrong end of cost-imposing strategies. In the East China Sea, for example, the Japan Self-Defense Force and Japan Coast Guard find themselves compelled repeatedly to react to Chinese incursions into Japanese airspace and territorial waters. Our competitors, by virtue of their geographic proximity and investments, have been able to use relatively inexpensive systems to counter relatively expensive and scarce U.S. capabilities. In many cases, they are able to control the pace and scope of action, forcing us to respond. Meeting this challenge does not involve fielding exotic new capabilities so much as retaining existing systems and employing them in innovative ways. The Department of Defense already has unmanned capabilities—as well as established UAS global infrastructure for support and operations—that are less expensive, have greater persistence, and pose less risk if lost than manned platforms that are well suited to conduct persistent surveillance. What is needed are new concepts of operations and organizations to employ them effectively to deter opportunistic aggression. The new concept, which we call “deterrence by detection,” will also benefit greatly from approaches that allow allies and partners to participate fully. If the United States fails to adapt, it risks falling victim to potentially catastrophic surprise in a future conflict. 14 Neither the Chinese nor the Russian armed forces use the term “anti-access/area denial,” although the Chinese do refer to “counter-intervention” capabilities. Both have focused their doctrine and force development on countering the ability of the United States to project military power against them. 6 CSBA | DETERRENCE BY DETECTION The Concept of “Deterrence by Detection” To meet the challenge of opportunistic aggression, this report outlines the concept of “deterrence by detection.” The logic that underpins the approach should be familiar to policemen and parents. It is that potential transgressors are less likely to act if they know they are being watched. Specifically, the concept of “deterrence by detection” rests on the premise that our adversaries are less likely to commit opportunistic acts of aggression if they know they are being watched constantly and that their actions can be publicized widely. Adversaries frequently seek to obscure their actions to prevent or delay a response, as the Russian government did when it initially denied its participation in Ukraine. The more they are able to do so, the greater the possibility that their actions will result in a fait accompli. Because of this, the ability to gather and disseminate real-time information is essential to deterring acts of aggression. An adversary’s attempts to interfere with or attack intelligence, reconnaissance, and surveillance (ISR) assets would provide evidence of aggressive intent. And if deterrence fails, reliable information can serve as the predicate for a political response and military action. The satellites and manned aircraft that the United States currently relies upon for ISR are very expensive and in many cases offer only periodic coverage of areas of interest. This study argues that there is a compelling need to develop innovative information-based concepts of operations based upon networks of unmanned aircraft systems. Creating enhanced ISR networks in the Western Pacific and Eastern Europe to detect and characterize Chinese and Russian “gray zone” activities and warn of an impending attack would improve the ability of U.S. and allied military forces to degrade, delay, and, if necessary, defeat aggression.15 The United States need to make these capabilities broadly available to America’s allies and partners so that they can contribute to deterrence. Intelligence information has long been used to deter and document undesirable activities. During the Cuban Missile Crisis, for example, the U. S. government publicly released highly classified U-2 reconnaissance photographs to demonstrate that, despite its denials, the Soviet Union was deploying nuclear-armed ballistic missiles to Cuba.16 A quarter century later, the U.S. Navy used surveillance footage to demonstrate that Iranian vessels were laying naval mines in the Persian Gulf before taking action against the vessel.17 More 15 Following Van Jackson, this report defines gray zone activities as “the use of tactics that challenge the status quo without resorting to war,” including “a broad class of events involving nonwar yet conflictual interactions—what might be considered ‘normal’ or ‘stable’ strategic competition.” Van Jackson, “Tactics of Strategic Competition: Gray Zones, Redlines, and Conflicts before War,” Naval War College Review 70, no. 3, Summer 2017, p. 39. 16 Dino A. Brugioni, Eyeball to Eyeball: The Inside Story of the Cuban Missile Crisis (New York: Random House, 1990). 17 John M. Broder and Michael Ross, “U.S. Says Attack Killed 3 Iranians: 26 Crewmen of Tehran Ship in Navy Custody,” Los Angeles Times, September 23, 1987, available at https://www.latimes.com/archives/la-xpm-1987-09-23-mn6331-story.html. www.csbaonline.org 7 recently, in June 2019 the U.S. government released surveillance footage documenting Iran’s role in attacks on foreign tankers in the Gulf of Oman.18 Beginning in the 1990s, military analysts such as Admiral William Owens argued that improvements in sensor and communication technology would produce “Dominant Battlespace Knowledge.” As Owens wrote in 2000, “By 2010…the U.S. military will be able to ‘see’ virtually everything of military significance [within a 200 by 200 mile box] in all weather conditions, and regardless of terrain… More important, the U.S. military commander will understand what he sees.”19 Although the United States has not yet reached Owens’s vision, it has taken impressive strides in that direction.20 Until now, real-time situational awareness was not available due to limited surveillance assets, lack of persistence, cost, absence of communications, and limitations to data processing. Today, the means to provide round-the-clock situational awareness exist, in the form of proliferated sensors backed by communication networks and data analytics. Indeed, today the ability to generate and maintain situational awareness—and deny the same to an adversary—is at the core of strategic and operational effectiveness. Implementing the concept of “deterrence by detection” will require an ISR network composed of systems that are cost-effective, persistent, and interoperable with a broad array of allies and partners. Any such network would include a variety of systems, including manned air, sea, and ground platforms; space assets; and cyber capabilities. Such a network would need to be supported by communications networks and feature recognition algorithms. In this report, we argue that UAS should play a critical role, particularly the current generation of non-stealthy, long-endurance UAS that possess wide-area surveillance capabilities.21 Although this argument might seem non-controversial, it contradicts the assumption made by many strategists that non-stealthy UAS cannot contribute much in the contested 18 Missy Ryan, Erin Cunningham, and Simon Denyer, “Trump Administration Steps up Efforts to Show Iran Carried Out Tanker Attacks,” The Washington Post, June 14, 2019, available at https://www.washingtonpost.com/ world/iran-slams-us-calls-claims-of-tanker-attackseconomic-terrorism/2019/06/14/b94c1ece-8e16-11e9-b6f4033356502dce_story.html. 19 Admiral Bill Owens and Ed Offley, Lifting the Fog of War (New York: Farrar Strauss Giroux, 2000), p. 119. 20 Thomas G. Mahnken, Technology and the American Way of War since 1945 (New York: Columbia University Press, 2008), chapter 6. 21 Colloquially referred to as drones, UAS have gone by various names over the years, underscoring the complexity of conceptualizing aircraft without human operators onboard and integrating them into existing military frameworks. In the past, DoD referred to UAS as remotely piloted vehicles (RPVs), emphasizing the role of the human pilot controlling the aircraft from afar. It later referred to them as unmanned aerial vehicles (UAVs), reflecting the diminishing role of the human and the increasingly automated nature of their operations. The shift in terminology from UAV to UAS reflected the fact that, as the Congressional Budget Office put it, “those complex systems include ground stations and other components besides the aircraft itself.” Congressional Budget Office, Policy Options for Unmanned Aircraft Systems, June 2011, p. 27. 8 CSBA | DETERRENCE BY DETECTION environments typically associated with operating against China or Russia.22 It also runs contrary to current U.S. Air Force plans to retire existing non-stealthy UAS. Real-time situational awareness is critical to countering the twin challenges of subconventional gray zone aggression and a conventional fait accompli gambit promptly and effectively. UAS conducting ISR missions could provide increased warning of a pending Chinese or Russian attack, thereby helping to ensure that forward postured forces are prepared to respond decisively. By increasing warning time, UAS would help mitigate the United States’ time-distance disadvantage, thereby allowing the United States and its allies to mass sufficient combat power to prevent a fait accompli. Force planners have often overlooked non-stealthy UAS in this sort of role because they consider them to be less survivable than other platforms in a contested or highly contested environment.23 Current generation UAS have operated predominantly over the more permissive battlefields of the Middle East. Certainly, any conflict between the United States and its allies on the one hand and China or Russia on the other would likely result in highly lethal and contested warfighting environments in either the Western Pacific or Eastern Europe, exactly where these UAS would operate. But since the aircraft would primarily function before the outbreak of major hostilities, they can be non-stealthy and yet still be effective. In fact, as argued below, their very visibility represents a key attribute in bolstering deterrence. Non-stealthy UAS would provide highly visible signals to friend and foe alike that any attempts at aggression in regions important to the United States and its allies might very well be detected in near real time. If Chinese or Russian leaders believed that U.S. and allied UAS might detect signs of aggression early enough and with enough clarity to spur an effective response, they might assess that the prospects of success were too uncertain and the potential costs too great to warrant action. In this scenario, costs would include not only the prospect of military failure but also reputational damage flowing from exposure of their plans. UAS could observe and document malign Chinese and Russian activities, providing the United States and its allies with evidence that would confirm culpability and justify subsequent countermeasures in the court of global public opinion. Given the prospect of such an unfavorable outcome, Chinese or Russian leaders might choose not to risk aggression in the first place, meaning deterrence would succeed from the American and allied perspective. Successful deterrence in this case does not require UAS to detect malign Chinese and Russian activities with 100 percent confidence. Rather, the probability of detection must merely be high enough to raise doubt in the minds of adversary leaders. Recent research on cyber operations, for example, has argued that a defender 22 Andrew Metrick, “Bad Idea: UAVs Aren’t Usable in Contested Environments,” Center for Strategic and International Studies, December 4, 2017, https://defense360.csis.org/bad-idea-uavs-contested-environments/. 23 For the definition of these terms, see Mark Gunzinger, Carl Rehberg, Jacob Cohn, Timothy A. Walton, and Lukas Autenried, An Air Force for An Era of Great Power Competition (Washington, DC: Center for Strategic and Budgetary Assessments, 2019). www.csbaonline.org 9 can cultivate a reputation for skill at surveillance to dissuade enemy aggression in contexts in which attack detection rates will never reach the threshold of perfection.24 The same logic applies to UAS operating in the Western Pacific and Eastern Europe. One final benefit of using UAS for persistent, wide-area surveillance ISR missions is that doing so would free up other ISR platforms to do things for which they are uniquely suited. For instance, space assets could focus on conducting reconnaissance of areas deep within Chinese and Russian territory, and 5th generation manned aircraft could focus on preserving their readiness for high-intensity contingencies. For the past two decades, manned aircraft have often been used to perform non-traditional ISR missions over conflict zones abroad, taking valuable resources and finite manpower away from other missions such as close air support and strike. Freeing up American military resources to perform their optimal tasks represents a subtle but important reason to retain non-stealthy UAS as a central component of U.S. and allied ISR networks. UAS Capabilities The DoD categorizes UAS into five groups based on size, range, speed, endurance, and general capabilities: Group 1: Typically hand-launched, self-contained, portable systems employed to support a small unit or base security. They are capable of providing “over the hill” or “around the corner” reconnaissance and surveillance. They operate within visual range and are analogous to radio-controlled model airplane... Group 2: Small to medium in size and usually used to support brigade and below intelligence, surveillance, reconnaissance, and target acquisition requirements. They usually operate from unimproved areas and launch via catapult. Payloads may include a sensor ball with electrooptical/infrared (EO/IR) and laser range finder/designator (LRF/D) capability. They typically perform special purpose or routine operations within a specific set of restrictions. Group 3: Operate at medium altitudes with medium to long range and endurance. Their payloads may include a sensor ball with EO/IR, LRF/D, signal intelligence (SIGINT), communications relay, and chemical biological radiological nuclear explosive (CBRNE) detection. They usually operate from unimproved areas and may not require an improved runway. Group 4: Relatively large UAS that operate at medium to high altitudes and have extended range and endurance. They normally require improved areas for launch and recovery, beyond line-of-sight (BLOS) communications, and have stringent airspace operations requirements. Payloads may include EO/IR sensors, radars, lasers, communications relay, SIGINT, Automatic Identification System (AIS), and weapons. 24 Jon R. Lindsay and Erik Gartzke, “Coercion through Cyberspace: The Stability-Instability Paradox Revisited,” in Kelly M. Greenhill and Peter Krause, eds., Coercion: The Power to Hurt in International Politics (New York: Oxford University Press, 2018). 10 CSBA | DETERRENCE BY DETECTION Group 5: Include the largest systems, operate at medium to high altitudes, and have the greatest range, endurance, and airspeed capabilities. They require improved areas for launch and recovery, BLOS communications, and the most stringent airspace operations requirements. Group 5 UAS perform specialized missions such as broad area surveillance and penetrating attacks.25 TABLE 1: UAS GROUP CLASSIFICATIONS AND CHARACTERISTICS Category Group 1 Group 2 Group 3 Group 4 Weight (lb) < 20 21 – 55 56 – 1,320 > 1,320 Group 5 > 1,320 *AGL=above ground level **MSL=mean sea level Normal Operating Altitude (ft) < 1,200 AGL* < 3,500 AGL < 18,000 MSL** Speed (kn) < 100 < 250 < 250 < 18,000 MSL Any speed > 18,000 MSL Any speed Representative UAS RQ-11 Raven, RQ-12 Wasp, RQ-20 Puma ScanEagle, Flexrotor RQ-7B Shadow, RQ-21 Blackjack MQ-8 Fire Scout, MQ-1C Gray Eagle, MQ-5 Hunter MQ-9 Reaper, RQ-4 Global Hawk, MQ-4C Triton Source: U.S. Joint Chiefs of Staff, “Joint Unmanned Aircraft Systems Minimum Training Standards,” last updated 4 September 2012, pg. 4, accessed at https://www.jcs.mil/Portals/36/Documents/Library/Instructions/CJCSI%203255.01.pdf?ver=2017-02-08-173223-063. Group 1 and 2 UAS, such as the RQ-11B Raven and MQ-27 Scan Eagle, have the shortest operational range and endurance.26 They are optimal for tactical reconnaissance missions or limited-scope military operations. Group 3 UAS, such as the RQ-7 Shadow and RQ-21 Black Jack, provide greater range and capability than Group 1 and 2 UAS. However, they lack the sensor payloads, weight capacity, and endurance for the missions emphasized in this study, namely continuous operations monitoring large geographic areas at great distances. As smaller UAS gain greater endurance, range, and payload capacity, they could play a more prominent role in surveillance networks, including in the Western Pacific. For the time being, however, Group 4 and 5 UAS are most suitable for the long-endurance, widearea surveillance missions required for the “deterrence by detection” operational concept. Supported by satellite communication (SATCOM) networks, Group 4 and 5 UAS can operate beyond line of sight (BLOS), maintain continuous orbits thousands of miles away from their bases, and remain on station for long periods of time without refueling. This study will focus on Group 4 and 5 UAS that fly at medium and high altitudes between 30,000 and 60,000 feet for periods of time ranging from 20 to 36 hours.27 25 Department of Defense UAS Task Force, Unmanned Aircraft System Airspace Integration Plan, March 2011, “Appendix D ‘UAS Elements and Groups,’” pp. D2-D3. 26 The aircraft naming convention identifies UAS with a “Q,” such as in RQ-4 and MQ-9. The first letter signifies the UAS’s mission, with “R” standing for “reconnaissance” and “M” standing for multi-role. The number at the end of the military aircraft nomenclature denotes the specific version or model in a series. 27 Congressional Budget Office, Policy Options for Unmanned Aircraft Systems, June 2011, p. 2. www.csbaonline.org 11 The following subsection describes theater-level high-altitude long-endurance (HALE) and medium-altitude long-endurance (MALE) UAS in the current U.S. inventory. Smaller UAS are much more mobile than larger UAS and can be launched by hand, catapult, or tube. By contrast, HALE and some MALE UAS require runways and clear line-of-sight (LOS) communications connected to ground stations for take-off and landing. Once in the air, however, large UAS operate using BLOS communication links to extend their ability to collect and disseminate information in real time. High-Altitude Long-Endurance (HALE) UAS RQ-4 GLOBAL HAWK (AIR FORCE) Source: U.S. Air Force available at https://www.af.mil/News/Photos/igphoto/2000336767/ The RQ-4 Global Hawk was born out of a project sponsored by the Defense Advanced Research Projects Agency (DARPA). The first Global Hawk flight took place in 2001: while still a developmental program, it flew in support of Operation Enduring Freedom.28 The Global Hawk’s versatility in payload integration stems from its open systems architecture. Its Universal Payload Adapter (UPA) gives the reconnaissance UAS the ability to carry a wide variety of payloads.29 For example, the National Aeronautics and Space Agency (NASA) has integrated and flown more than 30 different payloads on Global Hawks, demonstrating 28 Northrop Grumman, “Northrop Grumman’s Global Hawk System Marks 15 years of Supporting Warfighters,” November 17, 2016, https://news.northropgrumman.com/news/releases/northrop-grummans-global-hawk-systemmarks-15-years-of-supporting-warfighters. 29 Northrop Grumman, “Northrop Grumman Successfully Demonstrates Flexible Solution to Utilize Legacy and Future Sensors on RQ-4 Global Hawk,” February 25, 2016, https://news.northropgrumman.com/news/releases/northropgrumman-successfully-demonstrates-flexible-solution-to-utilize-legacy-and-future-sensors-on-rq-4-global-hawk. 12 CSBA | DETERRENCE BY DETECTION the UAS’s utility in gathering many types of information over a wide area for both military and civilian purposes. The Global Hawk is the U.S. Air Force’s theater-level reconnaissance UAS. It is capable of gathering near-real-time, high-resolution imagery of large areas of land in all types of weather, in the day or at night. The Global Hawk’s Enhanced Integrated Sensor Suite (EISS) includes a cloud-penetrating synthetic aperture radar (SAR) antenna, a ground moving target indicator (GMTI), a high-resolution electro-optical (EO) digital camera, and an infrared (IR) sensor.30 Human operators program flight plans for the Global Hawk’s reconnaissance routes but can task the UAS for ad hoc intelligence requirements mid-flight by inputting additional stops into the pre-programmed flight plan. The Global Hawk can also serve as a communications node. U.S. Air Force Global Hawks carry the Battlefield Airborne Communications Node (BACN), which translates and distributes voice communications and other battlespace information from numerous sources, geographically extending communication networks involving disparate users to provide improved situational awareness.31 Although it operates at high altitudes, the Global Hawk is not immune to attack. For example, in June 2019, the Iranian armed forces shot down a U.S. Navy RQ-4 Global Hawk operating in international airspace.32 MQ-4C TRITON (NAVY) Source: U.S. Navy available at https://www.navy.mil/view_image.asp?id=151812 30 Raytheon, “Global Hawk Integrated Sensor Suite,” accessed August 22, 2019, https://www.raytheon.com/capabilities/ products/globalhawk_iss. 31 Northrop Grumman, “Northrop Grumman Delivers BACN-Equipped Global Hawk to Air Force,” July 19, 2018, https:// news.northropgrumman.com/news/releases/northrop-grumman-delivers-bacn-equipped-global-hawk-to-air-force. 32 Jim Garamone, “Iran Shoots Down U.S. Global Hawk Operating in International Airspace,” U.S. Department of Defense news release, June 20, 2019, https://www.defense.gov/explore/story/Article/1882497/ iran-shoots-down-us-global-hawk-operating-in-international-airspace/. www.csbaonline.org 13 The MQ-4C Triton shares many of the same characteristics and capabilities of the RQ-4 Global Hawk, but is optimized for naval operations. Tritons collect imagery and signals intelligence information and detect, identify, and track maritime and littoral targets. MQ-4C Triton sensor data supports a range of naval missions, such as surface warfare, intelligence operations, strike warfare, maritime interdiction, and amphibious warfare.33 Originally developed as the Navy’s Broad Area Maritime Surveillance—Demonstrator (BAMS-D), the earliest versions of the Triton have operated since 2010 in missions supporting U.S. Navy 5th Fleet based in Bahrain.34 The MQ-4C Triton carries an electro-optical/infrared sensor to provide full-motion video and still imagery of surface targets.35 Equipped with the AN/ZPY-3 Multi-Function Active Sensor (MFAS), the MQ-4C Triton has a 360-degree active electronically scanned array radar, inverse synthetic aperture radar (ISAR), and maritime-surface-search (MSS) mode that permits persistent coverage of open oceans and littoral regions from extremely long ranges as well as the ability to track and classify maritime targets such as ships.36 Tritons are also equipped with the Multispectral Targeting Sensor; a communications intelligence (COMINT) and electronic intelligence (ELINT) sensor for characterizing and geo-locating integrated air defense systems (IADS); an Automatic Identification System (AIS) receiver that allows it to detect, locate, and track maritime vessels equipped with AIS transponders; as well as long-range, maritime surface-search radars for detecting unusual vessel movements.37 Together, these sensors aggregate disparate visual information and data to create a common operating picture that includes still images, full-motion video, and other maritime data such as the location of ships. Extreme platform persistence makes these sensors very powerful, especially when used in concert with low- earth orbit (LEO) satellites. The Navy established its first UAS squadron, VUP-19, in October 2016 and launched its first Early Operational Capability deployment of two MQ-4C Tritons to U.S. Navy 7th Fleet out of Andersen Air Force Base in Guam in September 2019. It is projected to achieve initial 33 Department of Defense Director, Operational Test & Evaluation (DOT&E), “MQ-4C Triton Unmanned Aircraft System (UAS),” FY15 Navy Programs, n.d., pp. 261–262, https://www.dote.osd.mil/pub/reports/FY2015/pdf/ navy/2015mq4c_uas.pdf. 34 Mark Pomerleau, “Future plans emerge for Navy’s Triton surveillance drones,” Defense News, April 9, 2018, https://www.defensenews.com/digital-show-dailies/navy-league/2018/04/09/future-plans-emerge-for-navystriton-surveillance-drones/. 35 “MQ-4C Triton Unmanned Aircraft System (UAS),” pp. 261-262. 36 Northrop Grumman, “AN/ZPY-3 Multi-Function Active Sensor (MFAS),” Northrop Grumman, last accessed August 22, 2019, https://www.northropgrumman.com/Capabilities/mfas/Pages/default.aspx. 37 “MQ-4C Triton Unmanned Aircraft System (UAS),” pp. 261-262. 14 CSBA | DETERRENCE BY DETECTION operational capability in 2021.38 Subsequent deliveries of the Triton will include a communications intelligence (COMINT) receiver and a sense-and-avoid (SAA) radar, which will help prevent the autonomously flying UAS from colliding with other aircraft and de-conflict air traffic.39 The Navy plans to station future orbits of the MQ-4C with the 7th Fleet in Guam; 6th Fleet in Sigonella, Italy; 5th Fleet in Bahrain; in Mayport, Florida; and on Whidbey Island, Washington.40 Medium-Altitude Long-Endurance (MALE) UAS MQ-1C GRAY EAGLE (ARMY) Source: U.S. Army available at https://asc.army.mil/web/portfolio-item/aviation_gray-eagle-uas/ The MQ-1C Gray Eagle is a variant of the MQ-1 Predator optimized for the needs of the U.S. Army. The Gray Eagle can carry a variety of payloads, such as electro-optical/infrared (EO/ IR) sensors, laser designators, synthetic aperture radar (SAR), communications relays, and missiles. Larger than the MQ-1 Predator but smaller than the MQ-9 Reaper, the MQ-1C Gray Eagle deploys with Combat Aviation Brigades to provide much of the same reconnaissance 38 Mark D. Faram, “Navy’s MQ-4C Triton community gets its very first squadron,” Navy Times, November 2, 2016, https://www.navytimes.com/news/your-navy/2016/11/02/navy-s-mq-4c-triton-community-gets-its-very-firstsquadron/; Paul McLeary, “Navy’s New Triton Drone Heads to Guam, New Pacific Recon Tool,” Breaking Defense, September 20, 2019, https://breakingdefense.com/2019/09/navys-new-triton-drone-heads-to-guam-new-pacificrecon-tool/; and Mark Pomerleau, “Navy stands up Triton drone training facility,” C4ISRNET, May 5, 2017, https:// www.c4isrnet.com/unmanned/uas/2017/05/05/navy-stands-up-triton-drone-training-facility/. 39 Chris Pocock, “Australia Confirms MQ-4C Triton Buy,” Aviation International News Online, June 28, 2018, https:// www.ainonline.com/aviation-news/defense/2018-06-28/australia-confirms-mq-4c-triton-buy. 40 Mark Pomerleau, “Future plans emerge for Navy’s Triton surveillance drones,” Defense News, April 9, 2018, https://www.defensenews.com/digital-show-dailies/navy-league/2018/04/09/future-plans-emerge-for-navystriton-surveillance-drones/. www.csbaonline.org 15 and light attack capabilities as its Predator predecessor. Transportable by C-130 aircraft, MQ-1C Gray Eagles have an endurance of over 27 hours, a range of 2,500 nm, and a maximum altitude of 29,000 ft.41 The aircraft possesses the ability to take off and land automatically, can be transported by standard Army trucks, and burns the same heavy fuel as its ground vehicles.42 U.S. Army Special Operations Forces and Intelligence and Security Command operate Gray Eagle Extended Range (ER) systems, which have an endurance of over 40 hours.43 The U.S. Army currently has two companies trained to operate the MQ-1C ER.44 MQ-9 REAPER (AIR FORCE) Source: U.S. Air Force available at https://media.defense.gov/2007/Oct/11/2000442365/-1/-1/0/070931-M-5827M-016.JPG The MQ-9 Reaper is faster, carries high-definition sensors, and can carry more and heavier weapons payloads than the MQ-1 Predator that it replaced.45 To support strike missions, the Reaper’s baseline includes the Multi-Spectral Targeting System (MTS), which integrates an 41 General Atomics Aeronautical, “Gray Eagle UAS,” last accessed October 25, 2019, http://www.ga-asi.com/gray-eagle. 42 Policy Options for Unmanned Aircraft Systems, pg. 21. 43 “MQ-1C Gray Eagle Unmanned Aircraft System (UAS).” 44 General Atomics, “Army Concludes New Equipment Training for Gray Eagle Extended Range,” last accessed October 25, 2019, http://www.ga.com/army-concludes-new-equipment-training-for-gray-eagle-extended-range. 45 Christian Clausen, “Air Force to Retire MQ-1 Predator Drone, Transition to MQ-9 Reaper,” U.S. Department of Defense news release, February 27, 2017, https://www.defense.gov/Newsroom/News/Article/Article/1095612/ air-force-to-retire-mq-1-predator-drone-transition-to-mq-9-reaper/. 16 CSBA | DETERRENCE BY DETECTION infrared sensor, color/monochrome daylight TV camera, image-intensified TV camera, laser range finder/designator, and laser illuminator.46 This robust suite of visual sensors allows the Reaper’s operators to view the data from its cameras as separate video streams or fused into one common operating picture. The UAS’s laser designator allows it to employ munitions such as the GBU-12 Paveway II and the AGM-114 Hellfire missiles, in addition to coordinateseeking weapons such as the Joint Direct Attack Munition (JDAM).47 The aircraft’s synthetic aperture radar (SAR) allows it to image targets at night and through weather for reconnaissance purposes. The MQ-9 Reaper is capable of hosting the latest generation of active and passive sensor technology to provide wide area surveillance data on par with that of legacy ISR platforms. The Reaper utilizes satellite communication links to acquire and relay real-time visual imagery and other intelligence to connected ground stations and BLOS nodes to support its reconnaissance missions. When used as an ISR asset, the Reaper collects target acquisition information in support of strike aircraft and ground commanders. Although the Reaper must take off and land with clear LOS to the ground control station (GCS), it can be piloted remotely using over-the-horizon communications through the Predator Primary Satellite Link (PPSL) and operate autonomously on a pre-assigned route if its command link is cut off. In this case, the Reaper could still remain on station, surveil an area of responsibility, distribute that information through a communications pod, and return to base through a pre-assigned route. Advantages and Disadvantages of UAS Any enhanced surveillance network employed in either the Western Pacific or Eastern Europe would likely incorporate a variety of ISR assets. Assessing the role of UAS in such a network requires understanding the comparative strength and weaknesses of UAS for such missions. Advantages of UAS First, UAS generally provide greater “time-on-station” persistence than satellites or manned aircraft. They possess the ability to persist over an area, which satellites in low-earth orbit do not. They also offer the ability to conduct longer uninterrupted missions than manned aircraft. This allows them to monitor conditions over a larger area for a longer period of time than manned alternatives. The long endurance UAS mentioned in the previous section can operate for over 30 hours without refueling. Future technological advancements in aerial refueling for UAS may eliminate the need for these UAS to land at all, except for scheduled maintenance. By contrast, U.S. regulations for military personnel prohibit Air Force pilots from flying more than 12 hours (14 hours with a waiver) in one 24-hour cycle for continuous 46 “MQ-1B Predator.” 47 U.S. Air Force, “Joint Direct Attack Munition GBU-31/32/38,” U.S. Air Force Fact Sheets, last updated June 18, 2003, https://www.af.mil/About-Us/Fact-Sheets/Display/Article/104572/joint-direct-attack-munition-gbu-313238/. www.csbaonline.org 17 operations.48 This amounts to a greater time on station compared to manned aircraft. For example, an MQ-9 in U.S. Air Force extended range configuration conducting a 1,000-nm persistent ISR mission could have a time on station of 25 hours, compared to 5 hours for a manned aircraft. Second, UAS can be less expensive than manned platforms. Without the need to design an airframe to accommodate a crew, UAS can be smaller and more efficient relative to manned aircraft. UAS can also be less expensive and more flexible than space-based reconnaissance platforms. To continue the scenario described above comparing unmanned ISR aircraft’s ability to conduct a 1,000-nm persistent ISR mission in 25 hours and a manned aircraft in 5 hours, the MQ-9 costs $12-15 million, compared to $145-220 million for a manned ISR aircraft. Moreover, cost and persistence advantages are multiplicative. The cost per flying hour of the MQ-9 is $4,864 and that of the RQ-4 is $18,591, compared to $41,064 for the E-3 Sentry, $54,922 for the RC-135 Rivet Joint, and $109,377 for the E-8 JSTARS.49 To extend the same scenario from one cycle of time on station to one year on station, it would cost $59 million per year to use an MQ-9 to maintain round-the-clock coverage of a 1,000-nm orbit, compared to $1.8 billion for a manned ISR aircraft to provide the same coverage. Although analysts continue to debate the relative costs of manned versus unmanned aircraft operations, numerous reliable studies have found that in many cases UAS cost less to procure and operate than manned systems.50 Third, unmanned systems eliminate the risk to human life inherent in manned aircraft. UAS can fly more dangerous missions without fear for the safety or health of a human pilot. In contested or highly contested environments, the lack of a human crew eliminates the risk of hostages or prisoners of war if the aircraft were to fall into enemy hands. This is not to say that unmanned systems eliminate risk altogether; however, unmanned systems provide additional escalation or de-escalation options to their operators. In the past few years, there have been several instances of unmanned aircraft being shot down over conflict areas. In 2017, U.S. forces in Syria twice shot down Iranian-made armed drones and Iranian armed forces shot down a U.S. Navy RQ-4 Global Hawk in 2019.51 In these instances, escalation dynamics may have been more likely to spiral into armed conflict had the downed aircraft been manned. 48 Department of the Air Force, “Air Force Guidance Memorandum to AFI 11-202V3, General Flight Rules,” October 3, 2019, p. 13 (Table 2.1 Maximum FDP [Hours]), https://static.e-publishing.af.mil/production/1/af_a3/publication/ afi11-202v3/afi11-202v3.pdf. 49 Industry estimate based on 2017 U.S. Department of Defense data 50 For studies comparing the costs of unmanned versus manned ISR aircraft, see Congressional Budget Office, Policy Options for Unmanned Aircraft Systems (Washington, DC: Congress of the United States, 2011). 51 Julian Borger, “US shoots down second Iran-made armed drone over Syria in 12 days,” The Guardian, 20 June 2017; Staff and agencies in Washington, “US shoots down pro-Assad drone that opened fire on coalition forces,” The Guardian, 8 June 2017; Jim Garamone, “Iran Shoots Down U.S. Global Hawk Operating in International Airspace,” U.S. Department of Defense press release, 20 June 2019, https://www.defense.gov/Explore/News/Article/ Article/1882497/iran-shoots-down-us-global-hawk-operating-in-international-airspace/. 18 CSBA | DETERRENCE BY DETECTION Finally, the use of UAS in military operations preserves the readiness and sustainability of manned systems and strengthens manned-unmanned teaming concepts. By relying on UAS to conduct initial persistent, wide-area searches and later cueing manned aircraft to conduct more focused follow-on searches, military commanders are able to conserve their manned forces for missions that do not suit UAS. For example, the U.S. Navy has teamed unmanned MQ-4C Tritons with manned P-8 Poseidons for maritime patrol missions. The MQ-4C and P-8 conduct cooperative ISR missions and are intended to replace the soon-to-be-retired EP-3 Airborne Reconnaissance Integrated Electronic System (ARIES) II, the signals reconnaissance version of the P-3 Orion.52 Operationally, the MQ-4C Triton conducts wide-area surveillance along a predetermined orbit. When it identifies unusual activity or a target of interest, the MQ-4C cues the P-8 to conduct focused searches. This kind of mannedunmanned teaming improves the U.S. military’s overall ability to operationalize, test, and improve manned-unmanned teaming concepts. Disadvantages of UAS UASs are not, of course, without weaknesses. For example, despite being able to remain in the air longer and reach farther destinations, UAS may be slower to reach their search areas, lack the ability to improvise or react quickly to unanticipated situations, and currently lack defensive measures to survive in contested environments. In addition, many reconnaissance UAS are non-stealthy and thus relatively easy for a determined adversary to destroy. This study argues, however, that the non-stealthy nature of existing theater-level reconnaissance UAS is what makes them useful as deterrents during peacetime. Conclusion This chapter has articulated the challenge posed by Chinese and Russian opportunistic aggression, a challenge that the current U.S. forces structure could meet but currently does not. It has also sketched out the concept of “deterrence by detection” as a promising solution to that challenge. Drawing on that foundation, the next chapter will describe the attributes of an enhanced ISR network to carry out “deterrence by detection”; discuss how it would operate in the Western Pacific and Eastern Europe, the two geographic theaters central most important to current U.S. defense strategy; and explore the role of allies and partners in such an approach. 52 Mark D. Faram, “Navy’s MQ-4C Triton community gets its very first squadron,” Navy Times, November 2, 2016, https:// www.navytimes.com/news/your-navy/2016/11/02/navy-s-mq-4c-triton-community-gets-its-very-first-squadron/. www.csbaonline.org 19 CHAPTER 2 Implementing the “Deterrence by Detection” Concept This chapter begins by describing the attributes of an enhanced ISR network designed to carry out the concept of “deterrence by detection” described in Chapter 1. It then identifies candidate geographic areas of interest for implementing the concept as a way of informing discussions of force structure and posture. Specifically, it argues that there are three priority geographic areas in the Asia-Pacific and three in Europe that are best suited for long-endurance unmanned aerial reconnaissance: the Taiwan Strait, South China Sea, and East China Sea in the Asia-Pacific and the Baltics, Black Sea, and eastern Mediterranean Sea in Europe. Next, the chapter estimates how many UAS would be needed to maintain persistent orbits, or regularly repeating paths around a target object or area, in those regions using existing military UAS. The discussion includes an assessment of how U.S. allies and partners might contribute to meeting the required UAS inventory. Finally, the chapter estimates the annual operating cost of the aircraft. Attributes of an Enhanced ISR Network In order to implement the concept of “deterrence by detection,” an ISR network should be visible, ubiquitous, affordable, and interoperable. 20 CSBA | DETERRENCE BY DETECTION FIGURE 1: ISR ARCHITECTURE USING UNMANNED AIRCRAFT SYSTEMS Proliferated LEO Satellites Laser Communications Laser Communications Ground Control Station EO/IR SAR SIGINT Suspicious Activity First, visibility is a key attribute of platforms in an ISR network designed to deter opportunistic aggression. Whereas there are many cases where it makes sense for ISR assets to operate covertly, in this case there is value in being overt. It is important for adversaries to know that they are being observed. Moreover, the task of “watching the watchers” would consume an adversary’s resources and could distract it from other, less visible operations. The fact that ISR aircraft are visible means they are vulnerable, and this vulnerability should also be seen as a valuable attribute. On the one hand, it offers an adversary the opportunity to attack the nodes of the surveillance network; on the other hand, doing so would shift the onus of escalation on the adversary. Attacking the network would be a concrete sign of aggressive intent. It would also be possible to build a self-defense capability into ISR systems, whether electronic warfare capabilities or active defense. Second, maintaining ubiquitous and ever-present presence is another key attribute of such a network. Whereas there are many cases where it makes sense for ISR assets to operate unpredictably to catch an adversary unaware, deterring through the threat of detection requires that a competitor have high confidence they are being observed. This implies that the ISR network should be composed of many rather than few ISR aircraft. Proliferating ISR assets will ensure that the loss of one or a few aircraft would not cause the network to fail. The need for ubiquitous, proliferated, and ever-present ISR networks makes UAS particularly attractive. As the cost of space launch continues to fall, these networks could be augmented by proliferated constellations of low-earth orbit satellites. www.csbaonline.org 21 Third, for an ISR network to provide the sort of ever-present, visible coverage needed to implement the concept of “deterrence by detection,” individual aircraft need to be affordable. This also favors UAS over manned aircraft under many circumstances. Finally, the argument in favor of including U.S. allies and partners in such a network is strong. In light of the changing military balances in the Western Pacific and Eastern Europe, it makes sense for the United States to seek new ways of reassuring its allies and friends and generating collective responses to crisis and aggression. An ISR network represents a promising approach to do just this. Moreover, as described below, a growing number of US allies and partners are interested in acquiring new ISR assets of their own, allowing them to share the responsibility for such a task. Although information-sharing agreements exist between the United States and its allies and partners, most are bilateral. By contrast, an enhanced ISR network would be open to all: states would contribute ISR assets and in return receive the common operating picture the network generated. Coalition ISR networks in the Western Pacific and Eastern Europe would have several advantages. First, they would provide the United States, its regional allies, and partners a common picture of potentially concerning activity in the area. The persistent nature of these wide-area surveillance operations would provide a “pattern of life” picture from which commanders could discern changes that might be of concern. Such a shared understanding may be a necessary precondition to collective action. Second, such an approach could represent a significant deterrent to hostile action—it would make it more difficult for an aggressor to act without being caught and an attack on the network would amount to an attack on all its members.53 As a result, the Department of Defense should place a priority on sharing the burden of ISR with allies and partners through a concerted effort to encourage the export of UAS. Such a network would be composed of proliferated airborne and space-based sensors linked together with high-bandwidth laser communications and using automated data processing algorithms to identify objects and events of interest. Sensors could include electro-optical and infrared (EO/IR) for target identification, synthetic aperture radar (SAR) for target classification at night and in all weather conditions, and moving target indication (MTI) to determine patterns of activity. Persistent EO/IR capabilities are especially important for observing and distributing visual evidence of malign actions by bad actors. High-bandwidth laser communications would knit the network together, while automated data processing would assist operators in maintaining situational awareness. 53 Thomas G. Mahnken, et. al., Asia in the Balance: Transforming US Military Strategy in Asia (Washington, D.C.: American Enterprise Institute, 2012), pp. 19–20. 22 CSBA | DETERRENCE BY DETECTION Priority Geographic Areas for ISR Missions The “deterrence by detection” concept should be implemented in different forms in separate theaters of operations. Some types of threat indicators, such as the slower process of island-building, require less frequent surveillance than would others, such as the amassing of amphibious forces on mainland China opposite Taiwan. This study categorizes the frequency of ISR revisit rates into four categories: persistent stare, persistent presence, periodic, and ad hoc. Persistent stare indicates that aircraft are surveilling objects or activities of interest in a target area non-stop for twenty-four hours a day, seven days a week. Persistent presence requires aircraft to visit objects or activities of interest in the target area multiple times per day but do not require 24/7 coverage. Aircraft flying in persistent presence orbits should be able to reroute their flight path to reach any other point in the target area within a few hours. Target areas requiring periodic revisit rates may not warrant persistent stare or persistent presence because the activities that are being observed stretch across longer periods of time. They do, however, require a continuous watch regular enough to track ongoing activities but unpredictable enough to prevent adversaries from avoiding detection by modifying their behavior according to predictable schedules. For example, the construction of artificial islands will not change significantly hour-by-hour but may show signs of change every few days or weeks. Finally, ad hoc revisit rates are at will and require the U.S. military to have reserve surge ISR capabilities ready to deploy in response to unexpected or unusual activities or objects of interest in target areas. Western Pacific In the Western Pacific, China continues to conduct hybrid operations against Taiwan in the politically sensitive Taiwan Strait and against U.S. allies and partners in the resource-rich, disputed waters of the South and East China Seas. Increasing the tempo and range of gray zone operations in these maritime areas, China has placed military equipment and forces on disputed islands; violated international and national airspace; jammed radars and GPS during U.S. allied military exercises; and harassed maritime vessels through patrols, interference, encirclement, and escort rackets. The imaginary line that runs through the middle of the Taiwan Strait has historically been the de facto 110-mile maritime boundary separating mainland China from Taiwan and has largely been treated as such by China and Taiwan. In April 2019, however, the People’s Liberation Army Air Force (PLAAF) crossed the median line with two of its J-11 fighter aircraft for the first time in about twenty years.54 The United States and its allies continue to conduct freedom of navigation operations (FONOPS) by sailing warships and warplanes through the Taiwan Strait median line. 54 Ketian Vivian Zhang, “China is pushing back against Taiwan for these three reasons,” The Washington Post, April 8, 2019, https://www.washingtonpost.com/politics/2019/04/08/china-is-pushing-back-against-taiwan-these-reasons/. www.csbaonline.org 23 The United States, its allies, and partners also conduct FONOPS in and around the South and East China Seas. These FONOPS have become especially important ever since the Chinese government began major land reclamation efforts in 2013 in the contested waters, building seven artificial islands and launching gray zone attacks against rival claimants. Rich in natural resources and located at the intersection of major maritime trade routes that span across the Indo-Pacific, the South China Sea hosts rival claims from Brunei, Indonesia, Malaysia, the Philippines, Taiwan, and Vietnam. The Spratly and Paracel Islands have been at the center of these territorial disputes but the Chinese government’s construction of seven man-made islands have further heightened tensions in the contested waters. China has installed military equipment on these islands, constructed runways capable of supporting military fighter and transport aircraft, and based air and maritime assets to expand its antiaccess/area-denial (A2/AD) architecture hundreds of miles beyond the Chinese mainland. In the East China Sea, five uninhabited islands are the object of a Chinese sub-conventional campaign. These five islands host rival claims by Japan, which calls them the Senkaku Islands and has exercised control over them for decades, and China, which calls them the Diaoyu Islands. Chinese gray zone aggression persists near these islands in the maritime areas between Japan’s contiguous (24 nm from land) and territorial (12 nm) waters. Armed Chinese vessels from its coast guard and maritime militia regularly sail within 12-24 nm of the islands and PLAN warships often loiter beyond the 24nm boundary.55 The PLAN has sailed its aircraft carrier, the Liaoning, several times across the Miyako Strait and the PLAAF regularly sends its fighters and bombers overhead, causing the Japanese Air Self-Defense Forces (JASDF) to conduct hundreds of sorties annually. In response, these hybrid operations have led Japan to construct a “wall” of military installations and “significantly [expand] its air force and coast guard bases centered on the southwestern island of Okinawa” to defend itself.56 Beyond these ongoing situations, there is also the possibility of a conflict between the United States and China in the Western Pacific over Taiwan, in the South China Sea, or in the East China Sea.57 55 Michael Macarthur Bosack, “China’s Senkaku Islands ambition,” The Japan Times, June 12, 2019, https://www. japantimes.co.jp/opinion/2019/06/12/commentary/japan-commentary/chinas-senkaku-islands-ambition/#. XbhXG5pKiUl. 56 Simon Denyer, “Japan builds an island ‘wall’ to counter China’s intensifying military, territorial incursions,” The Washington Post, August 21, 2019, https://www.washingtonpost.com/world/asia_pacific/ japan-builds-an-island-wall-to-counter-chinas-intensifying-military-territorial-incursions/2019/08/20/802bc282ae11-11e9-9411-a608f9d0c2d3_story.html. 57 This subsection draws on Mahnken et al., Tightening the Chain. If China launched multiple assaults simultaneously, say by staging an intra-theater feint to divert attention from its main objective, then conflict could unfold in multiple places. Future conflicts between the United States and China might also occur over North Korea or beyond the Western Pacific, particularly as Chinese interests and the PLA’s ability to protect them through power projection grow. In such cases, the PLAN would still need to sortie from bases on China’s coast through the First Island Chain. The PLA would also have to defend the Chinese homeland from attack as it conducted distant military operations. Understanding conflict scenarios in the First Island Chain is therefore essential whether war occurs there or further afield. 24 CSBA | DETERRENCE BY DETECTION Taiwan: The United States could become involved in a war across the Taiwan Strait if China attacked Taiwan and American leaders enforced the United States’ longstanding and public warnings that China not attempt to change the status quo through military force.58 The Chinese government’s 70-year-old political conflict with Taiwan continues to risk sparking a major conflagration. Although experts today disagree about China’s global ambitions, virtually all agree that China has one unwavering goal with respect to Taiwan: to reestablish political control over the island.59 Much of Chinese operational planning concerns Taiwan, which Chinese doctrine designates the “Main Strategic Direction.”60 China has developed military capabilities to persuade Taipei that it will suffer enormously if it bucks Beijing and convince the United States that aiding Taiwan would be costly and ultimately futile.61 Since Taiwanese President Tsai Ing-wen’s election in 2016, China has increased pressure on Taiwan in various ways, including by dispatching military aircraft and ships alarmingly close to Taiwan.62 The PLA has also improved its ability to conduct the complex joint operations required to attack Taiwan.63 Although some analysts have claimed that Taiwan can defeat a Chinese attack without U.S. assistance, that conclusion rests on overly optimistic assumptions about Taiwanese military capabilities.64 In short, Taiwan remains vulnerable to a Chinese attack, the cross-strait balance of military power is trending in China’s favor, and the United States would likely have to intervene militarily to stave off a Taiwanese defeat.65 South China Sea: China’s ongoing militarization of the South China Sea could trigger a conflict involving American forces. Since late 2013, China has reclaimed lands and constructed bases at sites it occupies in the Spratly and Paracel Islands. Some sites feature runways, hardened aircraft hangars, electronic jamming equipment, and anti-ship and 58 Bureau of East Asian and Pacific Affairs, “U.S. Relations With Taiwan,” U.S. Department of State Bilateral Relations Fact Sheet, August 31, 2018, available at https://www.state.gov/u-s-relations-with-taiwan/. 59 Michael A. Hunzeker and Alexander Lanoszka, A Question of Time: Enhancing Taiwan’s Conventional Deterrence Posture (Arlington, VA: Center for Security Policy Studies, Schar School of Policy and Government, George Mason University, 2018), pp. 35–41. 60 Academy of Military Sciences Strategic Research Department, Science of Military Strategy (Beijing: Academy of Military Sciences, 2013), pp. 198–199; and Liu Haijiang and Li Zhiyuan, eds., Research on Joint Tactical Thought (Beijing: Lantian Press, 2012), p. 156. 61 Oriana Skylar Mastro and Ian Easton, Risk and Resiliency: China’s Emerging Air Base Strike Threat (Washington, DC: Project 2049 Institute, 2017); and Ian Easton, The Chinese Invasion Threat: Taiwan’s Defense and American Strategy in Asia (Manchester, UK: Camphor, 2017). 62 Susan V. Lawrence, Taiwan: Select Political and Security Issues (Washington, DC: Congressional Research Service, October 2018), p. 2. 63 Office of the Secretary of Defense (OSD), Military and Security Developments Involving the People’s Republic of China 2018, annual report to Congress (Washington, DC: DoD, August 2018), pp. 96–97. 64 Travis Sharp and John Speed Meyers, “Correspondence: Will East Asia Balance Beijing?” International Security 43, no. 3, Winter 2018/2019, pp. 194–196. 65 Scott L. Kastner, “Is the Taiwan Strait Still a Flash Point? Rethinking the Prospects for Armed Conflict between China and Taiwan,” International Security 40, no. 3, Winter 2015/2016, pp. 69–74. www.csbaonline.org 25 air defense missiles.66 This infrastructure could support future Chinese offensive military operations. For example, the PLA might use it to anchor the assault and seizure of another contested feature that it does not occupy. The operation would signal military strength to the Chinese public, potentially distracting from domestic problems during an economic downturn or political scandal. China seizing any contested feature would trigger crisis, escalation, or potential war with other nations making territorial claims. Those nations would face intense political pressure at home not to accept China’s fait accompli. Besides attacking deliberately, Chinese militarization in the South China Sea risks inadvertent conflict since moving military and civilian assets around the islands could precipitate confrontations, whether planned or unplanned, between Chinese and other nations’ forces, including U.S. ships conducting freedom of navigation operations. East China Sea: China’s continued belligerence in its East China Sea territorial disputes with Japan could devolve into a war involving the United States given America’s unwavering commitment to its mutual defense treaty with Japan. Since 2012, Chinese Coast Guard and Maritime Militia vessels have intruded continuously into waters near the Senkaku Islands controlled by Japan. China has flown combat aircraft through Japanese airspace near the Senkakus and other islands, forcing Japan to scramble fighters to intercept them.67 With military forces shadowing one another in close proximity, one mistake by a ship captain or pilot could propel the nations into a militarized crisis. In the future, China could direct its militia or military forces to harass Japan in a predatory move to spur Japanese overreaction. Or the PLA could seize territory within the Senkakus, perhaps to demonstrate resolve during an escalating feud with Japan or the United States. Worse still would be a Chinese invasion of Japan’s Southwest Islands, a contingency that deeply worries Japan today. If the Chinese attack succeeded quickly, changing the status quo, Japanese and American leaders might face the difficult choice of having to escalate to restore the status quo ante bellum. In addition to the Taiwan Strait, South China Sea, and East China Sea, the ability to observe military activity persistently along the Chinese coastline would enhance situational awareness and could alert the United States and its Asian allies and partners to an impending Chinese attack. For example, persistent UAS orbits along the littoral areas of PLA’s Eastern and Southern theater commands could detect abnormal military activities, such as the amassing of PLA amphibious forces near Taiwan, which may signal an impending amphibious operation against Taiwan. Other geographic areas of interest in the Asia-Pacific include Bohai Bay and the Yellow Sea, which border northeastern China and the western littorals of the Korean Peninsula. Bohai Bay has been the site of PLA live-fire flight training exercises68, 66 Ronald O’Rourke, China’s Actions in South and East China Seas: Implications for U.S. Interests (Washington, DC: Congressional Research Service, August 2018), pp. 13–15. 67 Edmund J. Burke et al., China’s Military Activities in the East China Sea: Implications for Japan’s Air Self-Defense Force (Santa Monica, CA: RAND Corporation, 2018), pp. 9–15. 68 Edited by Huang Panyue, “Live-fire flight training near Bohai Bay,” China Military, November 2, 2018, http://eng. chinamil.com.cn/view/2018-11/02/content_9329880.htm. 26 CSBA | DETERRENCE BY DETECTION multi-day “military missions,”69 large-scale night-landing drills,70 and submarine-launched ballistic missile tests. Military activity inside mainland China is also of great interest to U.S. national security but these types of deep, hard-to-reach areas are better suited to other ISR platforms, such as satellites or stealthy penetrating aircraft. Unmanned aerial surveillance systems are well-suited to detecting a variety of activities that would serve as indicators and warning for Chinese opportunistic aggression in and around the Taiwan Strait, South China Sea, and East China Sea. Examples of such indicators include: • Movement of rocket forces, such as DF-21 and DF-26 anti-ship ballistic missiles, from peacetime garrisons; • Amassing of amphibious forces in Chinese ports near Taiwan; • Sorties of PLAN surface warships and supporting vessels; • Large-scale exercises; • Special forces deployments; • Deployment of out-of-area air forces and submarines; and • Implementation of force protection measures. Surveillance of China’s activities would also serve the purpose of monitoring, and thus potentially deterring, other opportunistic actors in those areas, such as North Korea and Russia. Eastern Europe In Europe, Russian hybrid operations target Eastern European countries due to the Russian leadership’s continued desire to dominate Russia’s near abroad, these states’ proximity to Russian military centers of gravity, and historical affinities to Russia among certain demographic groups. For this reason, U.S. allies and partners in the land and maritime areas that comprise and surround the Baltic states of Estonia, Latvia, and Lithuania; the Black Sea; and the eastern Mediterranean Sea are especially vulnerable to future Russian aggression, such as infiltrating bordering countries, encroaching on foreign territorial waters with submarines, violating airspace, and launching electronic warfare attacks on U.S. allied military systems. 69 China Military Online, “PLA to perform eight-day military missions in Bohai Sea and Yellow Sea,” People’s Republic of China Ministry of National Defense, July 17, 2015, http://eng.mod.gov.cn/DefenseNews/2015-07/17/content_4596616.htm. 70 Zhang Hong, “PLA staging large night-landing drills in Bohai, Yellow Sea,” South China Morning Post, November 19, 2013, https://www.scmp.com/news/china/article/1359803/pla-staging-large-night-landing-drills-bohai-yellow-seas. www.csbaonline.org 27 Except for a small land border between Lithuania and northeastern Poland, the Baltic states are isolated from the rest of continental Europe by the Russian exclave of Kaliningrad, the Russian sphere of influence in Belarus, and western Russian territory. Moreover, as a result of their Soviet history, significant segments of society in the Baltic states identify as Russian, carry Russian passports, and speak Russian as their first language.71 These Russian minorities in Estonia, Latvia, and Lithuania are concentrated mainly in the border areas near Russia and have caused concern for Baltic governments, especially following Russia’s campaigns in Crimea and eastern Ukraine. Because the Black Sea remains Russia’s only gateway to southern Europe, it continues to be important to monitor. The Black Sea is also the conduit through which Russia’s military transports its troops, equipment, and supplies to its naval facility in Tartus in western Syria. By establishing an expanding military presence in western Syria, Russia has gained a foothold into the eastern Mediterranean. The Baltic Region: The Baltic region is perhaps the most vulnerable to a Russian military fait accompli. A Russian conventional attack on or invasion of Estonia, Latvia, or Lithuania would trigger the collective defense provision embodied in Article 5 of the North Atlantic Treaty, leading the United States and its NATO allies to go to war against Russia in defense of the Alliance. NATO today is unprepared to defend the vulnerable Baltic states against a sudden Russian attack, especially in light of Moscow’s strengthening of its A2/AD capabilities and nuclear facilities in Kaliningrad and modernization of its ground maneuver units in its Western Military District in recent years.72 Similar to the situation in Georgia and Ukraine, Moscow could capitalize on stoking Russian nationalist sentiment among Russian minorities living in the Baltic states, fomenting political unrest and separatist movements as a pretext for direct military intervention. The Russian leadership could also take advantage of a civil crisis in the Baltic region as a distraction from political and economic problems at home if it perceives an opportunity to undermine the credibility and dismantle the unity of the Alliance. As the CSBA report Strengthening the Defense of NATO’s Eastern Frontier highlights, “the Russian government could determine that its best option during a significant crisis in the Baltic region is to risk a conventional attack on one or more of the Baltic states or even Poland because it believes it could quickly achieve its objectives and keep 71 Alistair Scrutton and David Mardiste, “Wary of divided loyalties, a Baltic state reaches out to its Russians,” Reuters, February 24, 2017, https://www.reuters.com/article/us-baltics-russia/wary-of-divided-loyalties-a-baltic-statereaches-out-to-its-russians-idUSKBN1630W2. 72 For more on U.S. and NATO current and future recommended force posture, see David A. Shlapak and Michael W. Johnson, Reinforcing Deterrence on NATO’s Eastern Flank (Santa Monica: Rand Corporation, 2016) and Alexander R. Vershbow and Philip M. Breedlove, Permanent Deterrence: Enhancements to the US Military Presence in North Central Europe (Washington, DC: Atlantic Council, 2019). For more on recent Russian military modernization developments, see Andrew Radin et al, The Future of the Russian Military: Russia’s Ground Combat Capabilities and Implications for U.S.-Russia Competition (Santa Monica: Rand Corporation, 2019); Keith Crane, Olga Oliker, and Brian Nichiporuk, Trends in Russia’s Armed Forces: An Overview of Budgets and Capabilities (Santa Monica: Rand Corporation, 2019); and Oren Liebermann, Frederik Pleitgen, and Vasco Cotovio, “New satellite images suggest military buildup in Russia’s strategic Baltic enclave,” CNN, 17 October 2018. 28 CSBA | DETERRENCE BY DETECTION the conflict short and limited.”73 The United States has invested over $16 billion since 2014 to enhance NATO’s ability to deter and defend against Russia, with much of that going to increasing pre-positioned stocks of equipment, rotational ground forces, infrastructure and bases, and exercises and training.74 Although these investments seek to deter Russia by raising the costs and risk of escalation, they do little to provide NATO with enhanced situational awareness and advance warning of a Russian sub-conventional attack that would alert military planners and political leaders of an impending attack and provide a wider range of military tools to respond to a Russian fait accompli. Black Sea: Although a direct military conflict between the United States and Russia in the Black Sea is unlikely, Russia could escalate ongoing hostilities and further expand its military presence in eastern Ukraine and northern Georgia and increase the threat to U.S. partners and NATO allies in the region, further normalizing Russian violations of national sovereignty and disregard for international rules and norms. Russian military activity in and around the Black Sea, particularly the naval operations of the Russian Black Sea Fleet, were central to Russia’s ability to wage war against Georgia in 2008, annex the Crimean Peninsula in 2014, and intervene in the Syrian war to shore up the authoritarian regime of Bashar al-Assad in 2015.75 Furthermore, Russia could use its military forces based in the Black Sea and Southern Military District to buttress its ongoing military operations in the Mediterranean Sea, outlined below, which poses a direct threat to the United States, its allies, and partners. Mediterranean Sea: Russia has sought to assert its influence by militarily intervening in conflicts in the Middle East and North Africa (MENA) region. It is also expanding its military presence beyond Russia’s southern flank, which could potentially lead to military confrontation with the United States, its allies, and partners; destabilization of the NATO Alliance; the prolonging of civil wars; and the erosion of U.S. influence in the region. The MENA region is at the center of global energy security with its abundance of oil and gas and U.S. and NATO counterterrorism efforts to defeat the Islamic State. The region has also seen civil wars backed by foreign powers like Russia and the United States and increased refugee and migrant flows to Europe, which have strained European resources and given rise to divisive populist movements across the continent.76 Moscow’s willingness to intervene militarily in the MENA region could alter a conflict’s trajectory in its favor, undercut the unity of the NATO Alliance, and provide fodder to fuel domestic political problems in Allied countries. 73 Billy Fabian, Mark Gunzinger, Jan van Tol, Jacob Cohn, and Gillian Evans, Strengthening the Defense of NATO’s Eastern Frontier (Washington, DC: Center for Strategic and Budgetary Assessments, 2019), p. 2. 74 U.S. Office of the Undersecretary of Defense (Comptroller), “European Deterrence Initiative: Department of Defense Budget Fiscal Year (FY) 2020,” March 2019, https://comptroller.defense.gov/Portals/45/Documents/defbudget/ fy2020/fy2020_EDI_JBook.pdf. 75 Igor Delanoe, Russia’s Black Sea Fleet: Toward a Multiregional Force (Arlington: Center for Naval Analyses, 2019), p. 1. 76 Steven Erlanger and Matina Stevis-Gridneff, “Why Europe is Finally Paying Attention to Libya,” The New York Times, 17 January 2020. www.csbaonline.org 29 Since 2015, Russia has sent military forces to back the Assad regime in Syria, refortified and renewed its lease for its only naval base in the Middle East at Tartus, and established new air and naval facilities in Latakia.77 Greater Russian presence in Syria increases the risk of U.S.-Russian military confrontation, such as the February 2018 attack on U.S. forces by proAssad Syrian forces and Kremlin-linked Russian mercenaries.78 Russia has also seized on opportunities to exacerbate existing tensions among NATO allies, such as by deepening the rift between the United States and Turkey by selling its S-400 missile defense system and brokering agreements with Turkey regarding Syria and Libya. Starting in September 2019, Russia has deployed hundreds of mercenary fighters to oppose the UN-backed provisional government in Libya through the Wagner Group, the private military company with close ties to the Kremlin that has also sent fighters to eastern Ukraine and Syria.79 This study identifies three areas in Eastern Europe that are best suited to the establishment of unmanned aerial reconnaissance networks: the Baltic states, the Black Sea, and the eastern Mediterranean Sea. These networks could detect indicators of Russian opportunistic aggression, such as: • Amassing airborne forces in Russia’s Western District for military exercises near the Russian border; • Reinforcing Kaliningrad; • Absence of demobilization after the end of a military exercise; • Prepositioning military forces in Belarus; • Preparing special forces raids; and • Deployment of Russian submarines. Implementing “Deterrence by Detection” The United States can implement the “deterrence by detection” concept with existing longendurance UAS platforms. This section outlines the results of CSBA analysis of a notional implementation strategy that uses existing ISR platforms to monitor developments in the priority geographic areas in the Western Pacific and Eastern Europe discussed above. 77 Yuras Karmanau, “Naval base in Syria anchors Russia to the Mediterranean,” The Navy Times, 26 September 2019. 78 Thomas Gibbons-Neff, “How a 4-Hour Battle Between Russian Mercenaries and U.S. Commandos Unfolded in Syria,” The New York Times, 24 May 2018. 79 Anas El Gomati, “Russia’s Role in the Libyan Civil War Gives It Leverage over Europe,” Foreign Policy, 18 January 2020; David D. Kirkpatrick, “Russian Snipers, Missiles and Warplanes Try to Tilt Libyan War,” New York Times, 7 November 2019; and Maggie Michael, “Libyan officials collect evidence of Russian fighters in war,” Associated Press, 5 December 2019. 30 CSBA | DETERRENCE BY DETECTION Western Pacific The Western Pacific is a vast expanse of maritime space situated at the crossroads of international trade routes, disputed sovereignty claims, and political tensions. The areas conducive to implementing deterrence by detection are the Taiwan Strait, East China Sea, South China Sea, and coastal areas of mainland China. In the Taiwan Strait, UAS would monitor the Taiwan Strait, provide periodic surveillance of China’s coastline, and surveil the waters farther to the east. Nearby in the East China Sea, UAS would continuously monitor the approaches to the Senkaku Islands. Coverage of the South China Sea orbit would be periodic and would include broad coverage of an area of roughly 260,000 nm2 as well as focused coverage of the Spratly Islands, which stand at the center of multiple territorial claims. FIGURE 2: SUGGESTED UAS ORBITS IN THE WESTERN PACIFIC Chinese coastal areas South China Sea East China Sea Senkaku Islands Taiwan Strait Spratly Islands Eastern Europe The geography of Eastern Europe is best-suited to enhanced ISR networks in three general areas: (1) the land and maritime areas near and around Poland and the Baltic states of Estonia, Latvia, and Lithuania, including the Baltic Sea and the Russian exclave of Kaliningrad; (2) the Black Sea and Ukraine; and (3) the eastern Mediterranean Sea near Syria. To surveil the eastern borders of Poland, the Baltic states, and eastern Kaliningrad, three persistent presence UAS orbits would cover roughly 30,000 nm2 of land around Russia’s western land borders. To patrol Kaliningrad’s western half and littoral areas touching the Baltic Sea, one persistent presence UAS orbit would complete the circle of surveillance above the Russian exclave and allow the United States and its NATO allies to www.csbaonline.org 31 detect unusual Russian conventional, paramilitary, or other sub-conventional activity. One persistent presence UAS orbit would surveil the Baltic Sea. The Black Sea has been the site of political and military hostilities between Russia and Ukraine and the source of tension between Russia and NATO. Russia, Ukraine, Romania, Bulgaria, Turkey, and Georgia all border the Black Sea. The strategic body of water is home to Russia’s Black Sea Fleet, which is based in Sevastopol, and played a critical role in facilitating Russian annexation of the Crimean Peninsula. One persistent presence UAS orbit around the Black Sea and along the north-south divide down central Ukraine cannot reverse Russia’s fait accompli in Crimea but can deter escalation or additional hybrid operations in eastern Ukraine and other Black Sea littoral areas. The third geographic area of priority conducive to deterrence by detection is in the eastern Mediterranean Sea near Syria. Covering roughly 125,000 nm2, this orbit would cover maritime areas stretching from Italy to Syria and between Southern Europe and North Africa. This orbit would provide periodic surveillance of the Russian naval facility in Tartus, the sole anchor of Russia’s military presence in the Middle East and the site of Russia’s burgeoning A2/AD architecture in the eastern Mediterranean. FIGURE 3: SUGGESTED UAS ORBITS IN EASTERN EUROPE Baltic Sea region Eastern European border areas Kaliningrad Ukraine and Crimea Belarus Black Sea Eastern Mediterranean and Syria 32 CSBA | DETERRENCE BY DETECTION Estimate of Required UAS Inventory TABLE 2: REQUIRED UAS INVENTORY FOR DETERRENCE BY DETECTION CONCEPT, BY GEOGRAPHIC AREA Western Pacific Orbit Area Revisit Rate Spratly Islands South China Sea Senkaku Islands Taiwan Strait Persistent Presence Periodic Persistent Presence Persistent Presence Chinese coastal areas Periodic Surge capabilities Ad Hoc Kaliningrad Persistent Presence Belarus, Eastern Europe Persistent Presence Baltic Sea Eastern Ukraine, Crimean Peninsula, Black Sea Eastern Mediterranean, Syria Persistent Presence Persistent Presence Periodic Surge capabilities Ad Hoc Search Area Base (nm2) 70,000 Japan 260,000 Singapore 50,000 Japan 10,000 Japan 90,000 75,000 Japan 5,000 Poland 15,000 15,000 30,000 Poland Poland Poland 40,000 Poland 80,000 Poland 125,000 Italy Base to Center (nm) 1,200 650 200 450 450 200 50 450 250 300 600 600 UAS Platform MQ-9 MQ-4C MQ-9 MQ-9 RQ-4 MQ-4C MQ-4C RQ-4 MQ-9 MQ-9 MQ-1C MQ-1C RQ-4 MQ-4C RQ-4 MQ-4C MQ-4C RQ-4 MQ-9 MQ-1C # of Orbits 1 1 1 1 1 2 1 1 4 1 1 1 1 1 1 1 1 1 1 1 # of UAS Per Orbit Total UAS 4 4 4 46 4 MQ-9 x 24 MQ-4C x 15 4 RQ-4 x 7 8 3 3 12 4 4 4 46 MQ-1C x 14 4 MQ-9 x 10 MQ-4C x 11 RQ-4 x 11 4 3 3 6 6 Europe Table 2 summarizes CSBA’s analysis of the UAS orbits, basing locations, aircraft types, and aircraft quantities required to implement the “deterrence by detection” concept in the Western Pacific and Eastern Europe. Additional UAS would be required for ISR missions beyond those described here.80 The UAS for the “deterrence by detection” concept would come from U.S., allied, and partner country inventories and would operate in national groups and potentially as part of a coalition network. CSBA analysis shows that 80 For recent CSBA assessments of overall UAS inventory requirements, see Gunzinger, et. al., An Air Force for An Era of Great Power Competition; Mark Gunzinger, Carl Rehberg, and Lukas Autenried, Five Priorities for the Air Force’s Future Combat Air Force (Washington, D.C.: Center for Strategic and Budgetary Assessments, 2020). www.csbaonline.org 33 implementing “deterrence by detection” would require 46 airframes in the Western Pacific and another 46 in Europe, for a total of 92 aircraft. The Western Pacific would require more MQ-9 Reapers to provide persistent presence over the localized flashpoints of the Taiwan Strait, Spratly Islands, and Senkaku Islands. The Western Pacific’s ocean environs would demand more of the maritime-optimized MQ-4C Tritons. For its part, Europe would require more ground-optimized MQ-1C Gray Eagles than the Western Pacific due to the overarching importance of air-ground operations in the European theater. The ad hoc surge capabilities held in reserve in each theater necessarily are a mix of the required UAS needed to maintain continuous orbits in the designated geographic areas of priority. The United States and its allies and partners could meet the inventory requirement by shifting existing aircraft from other theaters and missions to the Western Pacific and Europe and by assigning some of the aircraft the United States is already procuring to new missions. The decisions will depend on each aircraft’s production status and the size of the existing fleet. For example, the RQ-4 Global Hawk program has not procured new aircraft since FY 2012 and the U.S. Air Force received the last of its order of 45 Global Hawks in March 2019.81 The RQ-4 production line, however, is the same as the MQ-4C and plans to double its annual aircraft production capacity to 12 RQ-4 or MQ-4C per year are underway.82 The deterrence by detection strategy recommends 7 Global Hawks in the Western Pacific and 11 in Europe for a total of 18 RQ-4 in the Western Pacific and Europe. Thus, reaching the inventory goal of 18 Global Hawks, sourced solely from the United States, would depend on shifting forty percent of the existing fleet of 45 Global Hawks from the U.S. Air Force without having to procure new aircraft. However, with allied country contributions toward the total RQ-4 inventory goal, the number of required U.S. contributions would decrease while enhancing allied capacity-building and burden-sharing. Role of Allies and Partners Allies and partners have an important role to play in implementing “deterrence by detection,” both as operators of parts of regionally focused networks as well as consumers of the information they would produce. Some U.S. allies in the Western Pacific and Europe have already begun to purchase some of the UAS described in Chapter 1, sufficient quantities of which could augment or replace U.S. capabilities and ISR missions in those regions. Still, U.S. allies could invest further in these technologies and capabilities by increasing the number of existing long-endurance UAS in their inventory, whether they are U.S.-made or domestically produced. Other countries could also invest in them to boost their capabilities, further enhancing the global deterrence by detection strategy. 81 Garrett Reim, “Northrop Grumman to boost RQ-4 production capacity,” Flight Global, August 21, 2019. 82 Ibid. 34 CSBA | DETERRENCE BY DETECTION Asia-Pacific South Korea, Japan, and Australia are three U.S. allies that could contribute to the “deterrence by detection” concept in the Asia-Pacific and already operate or will soon operate MQ-1C Gray Eagles, MQ-9B Guardians, MQ-4C Tritons, and RQ-4 Global Hawks. Republic of Korea (ROK) To increase its situational awareness of North Korean military activity and areas around the Korean Peninsula, the U.S. Army permanently stationed MQ-1C Gray Eagles at Kunsan Air Base in March 2017. 83 Media sources reported that U.S. Forces Korea (USFK) will deploy six new MQ-1C Gray Eagle Extended Range drones to add to the six already-existing MQ-1C Gray Eagles deployed at Gunsan air base in September 2020.84 The Republic of Korea (ROK) is also seeking to fill a domestic capability gap by purchasing high-altitude unmanned ISR platforms for the ROK Air Force with the four RQ-4 Block 30 Global Hawks, the first of which arrived at Sacheon Air Force Base in December 2019.85 The Global Hawk’s wide-area surveillance capabilities “can detect around half of the North Korean territory, around 200 kilometers, from around the military demarcation line without getting inside North Korean airspace.”86 It will also strengthen South Korea’s Kill Chain pre-emptive strike system, one leg of the military’s three-axis air defense system, together with the Korean Air and Missile Defense (KAMD) and the Korea Massive Punishment and Retaliation (KMPR) plan. The Global Hawks are to be equipped with EO/IR, synthetic aperture radar, and ground moving target indicator (GMTI) sensors. Although these capability investments are directed at the conventional and nuclear threat emanating from North Korea, they could also be used as part of a deterrence by detection concept in the broader Western Pacific. South Korea’s first RQ-4 Global Hawk is set to deploy later in 2020 and the remaining three Global Hawks are slated to arrive in the first half of 2020.87 Japan Japan is the object of Chinese gray zone aggression in the East China Sea, leading the Japanese Self-Defense Force (JSDF) to consider ways to counter and deter these threats. Japan signed a contract for three RQ-4 Global Hawk Block 30 variants “fitted with an enhanced integrated sensor suite payload” in November 2018; the aircraft are scheduled to be delivered by September 1, 2022.88 According to Jane’s defense analysis, the Global Hawk is “too expensive to procure and operate in the numbers that Japan requires,” leading it to 83 Ed Adamczyk, “General Atomics to build parts, equipment for MQ-1C Gray Eagle drone,” United Press International, July 31, 2019. 84 Yu Yong-weon, “USFK to Deploy Advanced Killer Drones,” The Chosun Ilbo, 6 April 2020. 85 Oh Seok-min, “S. Korea brings in first Global Hawk unmanned aircraft,” Yonhap Daily News, 23 December 2019. 86 Ibid. 87 “S. Korea pushing to deploy Global Hawk aircraft this year,” Yonhap News Agency, 3 April 2020. 88 Gareth Jennings, “Japan signs for three Global Hawk UAVs,” Jane’s Defence Weekly, November 20, 2018. www.csbaonline.org 35 explore other potential long-endurance UAS options, such as the MQ-9B SkyGuardian and the Heron TP UAS from Israel.89 Australia By procuring MQ-4C Tritons for high-altitude surveillance of its oceans and MQ-9B SkyGuardians for medium-altitude surveillance of littoral regions and land combat, Australia has stepped up its surveillance efforts to monitor its areas of maritime responsibility, which make up about 10 percent of the world’s surface,.90 The Australian Defence Force (ADF) is responsible for monitoring the Pacific, Indian, and Antarctic oceans. To aid in this endeavor, the Australian government announced in March 2019 its plans to purchase seven MQ-4C Tritons for the Royal Australian Air Force (RAAF) and base them in the RAAF Base Edinburgh in southern Australia.91 Currently, the ADF “estimates Triton is capable of establishing a ten-hour orbit in the Southern Ocean, south of Heard Island, or similar efforts to the north of Guam and to the East of Fiji in the Pacific Ocean, from bases around the country.”92 Australia will receive the first of the aircraft in 2023.93 In addition, the Australian Government announced in November 2019 its decision to acquire MQ-9B SkyGuardians for the Australian Defence Force’s (ADF) Air 7003 project, making it Australia’s first armed medium-altitude long-endurance (MALE) UAS.94 According to the Australian Department of Defence, its military forces required a MALE UAS to enhance battlefield ISR and “land combat and amphibious warfare capabilities through improved situational awareness, firepower, protection, mobility and force sustainability.”95 The MQ-9B SkyGuardian complies with NATO type-certification requirements and other national civil aviation authorities, such as those in Australia and Europe. The UAS will support Australia’s overseas counter-terrorism capabilities and “augment search and rescue, humanitarian assistance and disaster relief and coastal surveillance tasks,” while being interoperable with allies and complementary to F-35 Joint Strike Fighters.96 Former Australian Defence Minister Christopher Pyne stated that Australia 89 Gareth Jennings, “Japan signs for three Global Hawk UAVs,” Jane’s Defence Weekly, November 20, 2018. See also “General Atomics to Conduct Flight Demonstrations of MQ-9 Guardian RPA in Japan,” Defense Post, 24 April 2018. 90 Nigel Pittaway, “Australia commits to Triton in $5 billion deal,” Defense News, June 27, 2018. 91 Royal Australian Air Force, “MQ-4C Triton Unmanned Aircraft System,” last accessed August 6, 2019, https://www. airforce.gov.au/technology/aircraft/intelligence-surveillance-and-reconnaissance/mq-4c-triton-unmanned-aircraft. 92 Pittaway, “Australia commits to Triton in $5 billion deal.” 93 Nigel Pittaway, “Northrop to deliver Triton drone to Australia in 2023, says Air Force official,” Defense News, February 27, 2019, https://www.defensenews.com/digital-show-dailies/avalon/2019/02/27/northrop-to-delivertriton-drone-to-australia-in-2023-says-air-force-official/. 94 Australian Government, Department of Defence, “Cutting edge remotely piloted platform chosen in billion dollar project,” November 28, 2019, https://www.minister.defence.gov.au/minister/lreynolds/media-releases/ cutting-edge-remotely-piloted-platform-chosen-billion-dollar. 95 Australian Government, Department of Defence, 2016 Integrated Investment Program, 2016, pg. 107, https://www. defence.gov.au/WhitePaper/Docs/2016-Defence-Integrated-Investment-Program.pdf. 96 Australian Government, Department of Defence, 2016 Integrated Investment Program, pg. 115. 36 CSBA | DETERRENCE BY DETECTION will acquire 12-16 armed MALE UAS with initial deliveries scheduled for the early 2020s and entry into service in the 2022-2023 timeframe.97 Europe Several NATO allies currently operate or will soon operate the MQ-9 Reaper; MQ-9B SkyGuardian; and RQ-4D Phoenix, NATO’s RQ-4 Global Hawk variant. Some countries are also considering acquiring the MQ-4C Triton. NATO NATO’s European members are on the front lines of defending against Russian aggression, and a deterrence by detection strategy incorporating NATO’s Alliance Ground Surveillance (AGS) system would enhance ongoing efforts to buttress deterrence along NATO’s eastern frontier. The NATO AGS system is a “fully NATO owned and operated system supported by the 28 Alliance nations” and “a key enabler of NATO’s joint intelligence, surveillance and reconnaissance capability.”98 Fifteen NATO allies are currently acquiring the AGS system and all twenty-eight NATO countries are financially contributing to the acquisition, installation, operations, and maintenance of the AGS system or providing interoperable ISR systems that will enable the smooth operation of the continent-wide surveillance system. An initial fleet of five RQ-4D, a variant of the RQ-4 Global Hawk, will “contribute to a range of missions such as protection of ground troops and civilian populations, border control and maritime safety, the fight against terrorism, crisis management, and humanitarian assistance in natural disasters.”99 The second of the five RQ-4D Phoenixes arrived in Italy in December 2019 and the remaining three aircraft are scheduled to be delivered throughout 2020.100 Initial operational capability (IOC) is expected to be reached in the first half of 2020 and full operational capability by 2023.101 97 Nigel Pittaway, “Australia makes its pick for drone fleet,” Defense News, November 16, 2018. 98 “NATO’s Alliance Ground Surveillance System Featured at NATO Warsaw Summit,” Northrop Grumman, July 8, 2016, https://news.northropgrumman.com/news/releases/nato-s-alliance-ground-surveillance-system-featuredat-nato-warsaw-summit. 99 NATO, “Alliance Ground Surveillance (AGS),” last updated June 21, 2019, https://www.nato.int/cps/en/natohq/ topics_48892.htm. 100 Allied Air Command Public Affairs Office, “Second NATO Alliance Ground Surveillance Aircraft Arrives in Europe,” NATO Allied Air Command, 19 December 2019, https://ac.nato.int/archive/2019/page87504618.aspx. 101 David Cenciotti, “NATO Receives Second RQ-4D ‘Phoenix’ Remotely Piloted Vehicle At Sigonella Air Base, Italy,” The Aviationist, 19 December 2019, https://theaviationist.com/2019/12/19/nato-receives-second-rq-4d-phoenix-remotelypiloted-vehicle-at-sigonella-air-base-italy/. www.csbaonline.org 37 Belgium In March 2019, the U.S. State Department approved the sale of four unarmed MQ-9B SkyGuardians, two ground control stations (GCSs), and related equipment to Belgium.102 Deliveries are scheduled for 2022-2024 and full operational capability for 2025.103 France In 2013, France requested up to 16 MQ-9 Reapers, 8 mobile ground control stations (GCSs), and related equipment and training.104 France sought medium-altitude long-endurance (MALE) capabilities to “provide for the defense of its deployed troops, regional security, and interoperability with the U.S… [and] meet current and future threats by providing improved ISR coverage that promotes increased battlefield situational awareness, anticipates enemy intent, augments combat search and rescue, and provides ground troop support.”105 France ended up purchasing 12 unarmed MQ-9 Reapers in 2017.106 By November 2021, the French Air Force will arm its fleet of MQ-9 Reapers with GBU-12 and AGM-114 Hellfire air-tosurface missiles.107 Germany To enhance its maritime surveillance capabilities and fill its signals intelligence (SIGINT) capability gap, Germany planned to acquire Euro Hawks, SIGINT-dedicated variants of the RQ-4 Global Hawk, but the $700 million program ended after Germany failed to acquire regulatory certification permitting the military UAS to fly in European civilian airspace.108 In April 2018, the U.S. Defense Security Cooperation Agency notified Congress of a possible foreign military sale to Germany of four MQ-4C Tritons.109 German officials previously defended the potential $2 billion purchase by “arguing the U.S. work on flight-safety issues was more advanced than German efforts” so “the U.S. Navy’s certifications to that effect would be more or less applicable to Europe.”110 However, in January 2020, the German 102 U.S. Defense Security Cooperation Agency, “Belgium—MQ-9B SkyGuardian Remotely Piloted Aircraft (RPA),” 26 March, 2019, https://www.dsca.mil/major-arms-sales/belgium-mq-9b-skyguardian-remotely-piloted-aircraft-rpa. 103 Gareth Jennings, “Belgium approved for SkyGuardian,” Jane’s Defence Weekly, 26 March, 2019. 104 U.S. Defense Security Cooperation Agency, “France—MQ-9 Reapers,” 27 June 2013, https://www.dsca.mil/ major-arms-sales/france-mq-9-reapers. 105 Ibid. 106 Agence France Presse, “U.S. Readies Sale of Reaper Drones to France,” Huffington Post, Last updated 6 December 2017. 107 Gareth Jennings and Emmanuel Huberdeau, “France begins process of arming Block 5 Reapers,” Jane’s Defence Weekly, 29 October 2019. 108 Sebastian Sprenger, “‘Euro Hawk’ fiasco looms large in Germany’s new spy drone search,” Defense News, May 25, 2018, https://www.defensenews.com/unmanned/2018/05/25/euro-hawk-fiasco-looms-large-in-germanys-newspy-drone-search/. 109 U.S. Defense Security Cooperation Agency, “Germany – MQ-4C Triton Unmanned Aircraft Systems (UAS),” April 5, 2018, https://www.dsca.mil/major-arms-sales/germany-mq-4c-triton-unmanned-aircraft-systems-uas. 110 Sprenger, “‘Euro Hawk’ fiasco looms large in Germany’s new spy drone search.” 38 CSBA | DETERRENCE BY DETECTION government cancelled its $2.5 billion plans to purchase the MQ-4C Triton, citing budgetary and procurement timeline concerns.111 Italy Italy has acquired a fleet of six unarmed MQ-9 Reapers for its Air Force and in 2015 decided to equip them with weapons.112 While flying over Libya in support of Operation Mare Sicuro’s human trafficking surveillance, the Italian Air Force lost contact with one of its MQ-9 Reapers, which subsequently crashed.113 The Netherlands In 2015, the U.S. State Department approved the sale of four MQ-9 Reapers and associated equipment and training to the Netherlands.114 Starting in December 2018, crews from the Royal Netherlands Air Force began training in New Mexico to fly and operate its unarmed Reapers.115 Delivery of the aircraft is expected to be completed by December 2020.116 Spain In 2015, the U.S. State Department approved the possible sale of four MQ-9 Reapers and associated equipment and training to Spain, and the Spanish Air Force received its first delivery of aircraft in December 2019.117 The Spanish government chose the Reapers to increase its interoperability with the United States and other NATO allies, such as the United Kingdom, France, and Italy. The Spanish Air Force intends to use the MQ-9 Reapers in “homeland security, peacekeeping, peace enforcement, counterinsurgency, and counterterrorism operations.”118 111 Sebastian Sprenger, “Germany walks away from $2.5 billion purchase of US Navy’s Triton spy drones,” Defense News, 28 January 2020. 112 U.S. Defense Security Cooperation Agency, “Italy—Weaponization of MQ-9s,” 4 November 2015, https://www.dsca. mil/major-arms-sales/italy-weaponization-mq-9s. 113 Tom Kington, “Italy confirms military drone crashed in Libya,” Defense News, 20 November 2019. 114 U.S. Defense Security Cooperation Agency, “The Netherlands—MQ-9 Reapers,” 6 February 2015, https://www.dsca. mil/major-arms-sales/netherlands-mq-9-reapers; see also U.S. Defense Security Cooperation Agency, “Netherlands signs deal for unarmed MQ-9 Reaper drones,” 17 July 2018, https://www.dsca.mil/news-media/news-archive/ netherlands-signs-deal-unarmed-mq-9-reaper-drones. 115 “General Atomics awarded $123 million Netherlands MQ-9 Reaper drone contract,” The Defense Post, 22 March 2019. 116 U.S. Department of Defense, “Contracts for March 21, 2019,” 21 March 2019, https://www.defense.gov/Newsroom/ Contracts/Contract/Article/1792112/. 117 “GA-ASI Predator B/MQ-9 Reaper/MQ-9B,” Jane’s IHS, Last updated 23 December 2019, https://janes.ihs.com/ Janes/Display/juav9266-juav. 118 U.S. Defense Security Cooperation Agency, “Spain—MQ-9 Block 5 aircraft,” 6 October 2015, https://www.dsca.mil/ major-arms-sales/spain-mq-9-block-5-aircraft. www.csbaonline.org 39 United Kingdom The United Kingdom is in the process of acquiring at least 16 MQ-9B Protector RG Mk1, the Royal Air Force’s (RAF) version of the MQ-9B SkyGuardian, which will replace the RAF’s MQ-9 Reaper fleet. The acquisition of the MQ-9B Protector makes the United Kingdom the first customer for the MQ-9 Reaper variant type certified to fly in European civilian airspace.119 The first test and evaluation Protector UAS will be delivered most likely in 2021 with initial operational capability in November 2023.120 Partners Beyond America’s allies, partner nations should also be encouraged to participate in ISR networks. Becoming a member of such a network would provide states with valuable information about activities in and around their territory and would give them an expanded set of options to protect their sovereignty. The United States would need to be able to export its UAS widely to facilitate such cooperation. In Asia, for example, states such as Malaysia, Singapore, Indonesia, and Vietnam might find it acceptable to participate in a multinational ISR network even if they are unwilling to participate in other military activities. In the greater Indo-Pacific, official negotiations between the United States and India on the purchase of MQ-9 Reaper variants for the Indian Air Force, Army, and Navy have been ongoing since at least 2016 but have been mired in delays and changes to specifications regarding quantity and type of UAS. Originally, India was set to acquire 22 MQ-9 Reaper variants optimized for maritime surveillance, but reports indicate that the U.S. Defense Department and Indian Ministry of Defense are working to customize a MQ-9 Reaper variant for standardized use among the Indian Air Force, Army, and Navy.121 However, senior Indian Ministry of Defense officials stated that India’s limited defense budget will delay any U.S. weapons purchases until 2021 or 2022.122 119 Beth Stevenson, “ ‘Gamechanger’ aerial drone arrives in UK after mammoth 24-hour transatlantic flight,” Defense News, 13 July 2018. 120 Andrew Chuter, “British Defence Ministry reveals why a drone program now costs $427M extra,” Defense News, 24 January 2020. 121 Theresa Hitchens, “India-US ‘Tailoring’ Predator UAV For Multi-Service Buy,” Breaking Defense, 28 August 2019. 122 Vivek Raghuvanshi, “New weapons purchases suffer under India’s latest defense budget,” Defense News, 4 February 2020. 40 CSBA | DETERRENCE BY DETECTION Estimate of Budgetary Costs The table below estimates the number of UAS, provided by the United States and its allies, required to implement the deterrence by detection operational concept. TABLE 3: REQUIRED UAS INVENTORY FOR DETERRENCE BY DETECTION CONCEPT BY AIRCRAFT TYPE Aircraft Western Pacific Eastern Europe Total MQ-9 Reaper 24 10 34 MQ-4C Triton 15 11 26 RQ-4 Global Hawk 7 11 18 MQ-1C Gray Eagle 0 14 14 Total 46 46 92 Table notes: Data adapted from Table 1. As Table 3 shows, the total number of UAS airframes needed to implement a “deterrence by detection” strategy in the Asia-Pacific and European theaters is well within reach. If sourced solely from the U.S. aircraft inventory across the Air Force, Navy, and Army, the 92 total UAS dedicated to the concept would represent 15 percent of the pool of MQ-9, MQ-4C, RQ-4, and MQ-1C in the U.S. inventory. Broken down, this concept would require 14 percent of the Air Force’s MQ-9 Reapers, 38 percent of the Navy’s MQ-4C Tritons, 53 percent of the Air Force’s RQ-4 Global Hawks, and 6 percent of the Army’s MQ-1C Gray Eagles.123 Indeed, a virtue of the concept is that it employs capabilities that the United States already possesses but that have been underutilized in the context of great-power competition because their value in that context has not been appreciated. Contributions from allied countries would reduce the burden on the U.S. military and free up UAS for other missions while enhancing allied capabilities. 123 Currently, there are 251 MQ-9A Reapers in the U.S. Air Force, 68 MQ-4C Tritons in the U.S. Navy program of record, 34 RQ-4B Global Hawks in the U.S. Air Force, and 162 MQ-1C Gray Eagles in the U.S. Army. For the MQ-9A Reaper and RQ-4B Global Hawk, see “2019 USAF Almanac: Equipment, Aircraft Total Aircraft Inventory (TAI),” Air Force Magazine, 30 September 2018, https://www.airforcemag.com/PDF/MagazineArchive/Magazine%20Documents/2019/ June%202019/0619_Equipment.pdf. For the MQ-4C Triton, see U.S. Department of Defense, “MQ-4C Triton Unmanned Aircraft System (MQ-4C Triton),” Selected Acquisition Report, December 2015, p. 37, https://www.esd.whs.mil/ Portals/54/Documents/FOID/Reading%20Room/Selected_Acquisition_Reports/16-F-0402_DOC_71_MQ-4C%20 Triton_DEC_2015_SAR.pdf. The MQ-4C reached early operational capability in January 2020 and is estimated to reach initial operational capability (IOC) in February 2021 and full rate production (FRP) in May 2021. For the MQ-1C Gray Eagle, see International Institute for Strategic Studies, “United States: U.S. Army,” The Military Balance 2020 (International Institute for Strategic Studies: London, 2020), p. 48. www.csbaonline.org 41 We estimate that the annual operating cost for the 92 UASs would total approximately $1.4 billion per year, based on Congressional Budget Office figures.124 Since the aircraft would come from the existing inventory, not from new purchases, the operating cost represents money DoD would have spent anyway to keep the aircraft flying (assuming it kept them flying). For this reason, implementing “deterrence by detection” should not require any spending increases. Rather, implementing the concept should only require DoD to change what it does with the aircraft it already pays for. Split among the United States and its many allies and partners in the Western Pacific and Europe, the estimated cost per country should remain affordable relative to the expected security gains. The operating cost includes the direct and indirect expenses of flying and maintaining the aircraft. However, it does not necessarily reflect every enabling asset required to set up and administer an ISR architecture, to include data links; processing, exploitation, and dissemination (PED) throughput; contractor support; and many other activities. Estimating these additional costs lies outside the report’s scope. Conclusion The United States and its allies face operational challenges in competing against China and Russia, including the ability to deter opportunistic acts of aggression by sub-conventional forces that would result in a fait accompli. The innovative operational concept of “deterrence by detection,” the idea that our adversaries are less likely to commit opportunistic acts of aggression if they know they are being watched constantly and that their actions can be publicized widely, can generate and maintain real-time situational awareness that can contribute to solving the fait accompli challenge. Unmanned ISR aircraft capable of conducting wide-area persistent surveillance missions are best suited to the implementation of “deterrence by detection” by the United States, its allies, and partners. Although this concept is far from the panacea that will deter and deny our adversaries the ability to achieve a conventional fait accompli, it is a realistic, effective, and affordable step in the right direction. 124 This estimate multiplies the UAS inventories in Table 3 by the direct and indirect cost figures included in Congressional Budget Office, The U.S. Military’s Force Structure: A Primer (July 2016), p. 100. Due to data limitations, the estimate assumes the MQ-4C has the same operating cost as the RQ-4. The estimate converts CBO’s per squadron cost to per aircraft cost and adjusts the figures to FY 2019 dollars based on DoD, National Defense Budget Estimates for FY 2019 (April 2018), Table 5-6, pp. 62-63. The calculation proceeds as follows: (34 MQ-9s x $7.8m) + (26 MQ-4Cs x $25.1m) + (18 RQ-4s x $25.1m) + (14 MQ-1Cs x $4.3m) = ~$1.4b. 42 CSBA | DETERRENCE BY DETECTION LIST OF ACRONYMS A2/AD anti-access/area denial ADF Australian Defence Force AESA active electronically scanned array radar AGS Alliance Ground Surveillance AIS Automatic Identification System ASBM anti-ship ballistic missile ASCM anti-ship cruise missile ASW anti-submarine warfare BACN Battlefield Airborne Communications Node BAMS-D Broad Area Maritime Surveillance-Demonstrator BLOS beyond line-of-sight C4ISR �command, control, communications, computers, intelligence, surveillance, and reconnaissance CBRNE chemical, biological, radiological, nuclear, explosive CCD camouflage, concealment, and deception CCP Chinese Communist Party COMINT communications intelligence CONUS continental United States DARPA Defense Advanced Research Projects Agency DoD Department of Defense ECS East China Sea EISS Enhanced Integrated Sensor Suite ELINT electronic intelligence EO/IR electro-optical/infrared GCS ground control station HALE high-altitude long-endurance IADS integrated air defense systems IAMD integrated air and missile defense ISAR inverse synthetic aperture radar ISR intelligence, surveillance, reconnaissance JDAM Joint Direct Attack Munition KAMD Korean Air and Missile Defense km kilometers KMPR Korean Massive Punishment Retaliation LEO low-earth orbit LOS LPI/LPD LRASM MALE MFAS MSS MTI NASA NDS nm PED PLA PLAAF PLAN PPSL RAAF ROK SAA SAR SATCOM SCS SIGINT UAS UPA UUS line-of-sight low probability of intercept/detection Long-Range Anti-Ship Missile medium-altitude, long-endurance multi-function active sensor maritime-surface-search moving target indication National Aeronautics and Space Agency National Defense Strategy nautical miles processing, exploitation, dissemination People’s Liberation Army People’s Liberation Army Air Force People’s Liberation Army Navy Predator Primary Satellite Link Royal Australian Air Force Republic of Korea sense-and-avoid synthetic aperture radar satellite communications South China Sea signals intelligence unmanned aircraft system universal payload adapter unmanned underwater vehicle www.csbaonline.org 43 1667 K Street, NW, Suite 900 Washington, DC 20006 Tel. 202.331.7990 • Fax 202.331.8019 www.csbaonline.org